1. What is Brute force?
Brute force, also known as exhaustive search attack, is a technique hackers employ to test millions of username, password, or encryption key combinations until the correct one is identified. This classic approach retains its effectiveness because many systems still suffer from authentication vulnerabilities or rely on weak passwords.

A brute force attack is typically automated using software capable of executing hundreds of thousands of attempts per second. Hackers target user accounts, enterprise networks, or even encrypted data decryption. The term "brute force" aptly captures its essence: leveraging raw computational power to breach security barriers rather than sophisticated exploits.
2. Common brute force attack variants
The following outlines prevalent brute force attack types encountered by individuals and organizations alike. Recognizing the characteristics of each variant enables early detection and the selection of appropriate defensive measures.
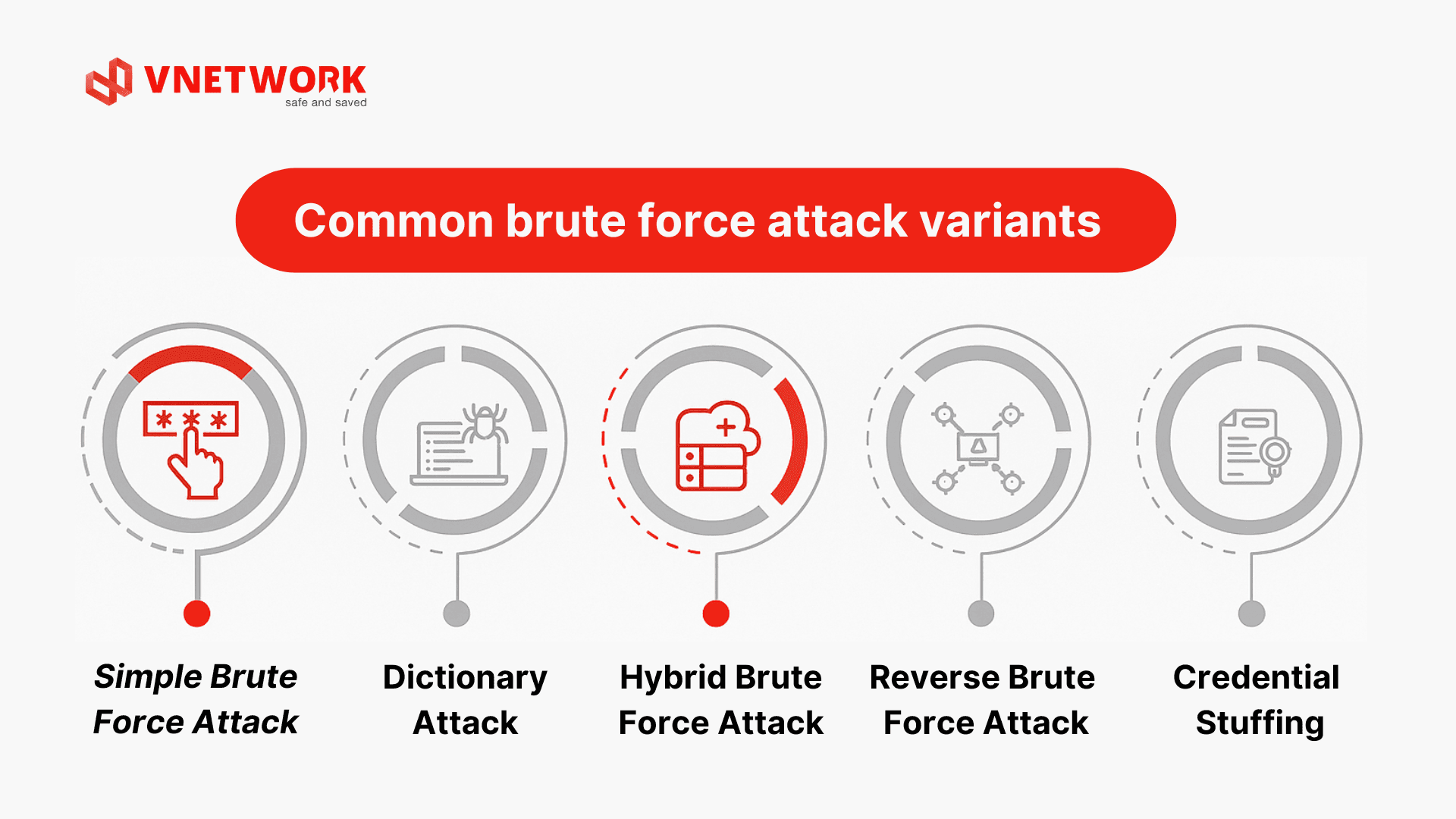
2.1. Simple brute force attack
This foundational form involves manually testing common passwords such as "123456", "password", or "admin". Though straightforward, it proves effective against users with weak or reused credentials.
2.2. Dictionary attack
Hackers utilize a predefined wordlist containing millions of common terms and characters, augmented with numbers or special symbols to guess passwords. Examples include "football", "football123", or "Football@2024".
Although less advanced than modern techniques, dictionary attacks enable rapid probing of simplistic passwords.
2.3. Hybrid brute force attack
This combines dictionary attacks with traditional brute force. Attackers start with popular word lists and automatically append characters, numbers, or birth years to expand guessing possibilities.
2.4. Reverse brute force attack
Rather than targeting usernames first, hackers begin with a known password (often from leaked datasets) and scan for matching accounts. For instance, with "Password123", they probe millions of usernames to identify matches.
2.5. Credential stuffing
Exploiting password reuse across platforms, attackers apply credential pairs leaked from site A to attempt logins on site B. If a user shares the same password for Gmail and Facebook, a single breach can compromise multiple accounts.
3. Objectives and consequences of brute force attacks
Brute force attacks extend beyond mere password guessing; they pursue deliberate goals with severe repercussions. Understanding attacker motivations and business impacts empowers organizations to adopt proactive prevention and response strategies.
3.1. Attacker objectives
Malicious actors deploy brute force with specific aims, often for profit or to enable deeper intrusions:
- Monetize through advertising or traffic redirection: Compromise accounts or websites to inject malicious ads, redirect users to revenue-generating pages, or install spyware for behavioral data collection.
- Steal sensitive data: Gain access to financial information, customer records, or internal files, which may be sold on dark markets or used for extortion.
- Distribute malware and build botnets: Install backdoors or malware post-breach to incorporate servers or devices into botnets for DDoS campaigns or larger operations.
- Seize system control: Target administrative privileges to alter website content, inject exploits, or manipulate data.
- Damage reputation or strategic interests: Sabotage brands by posting objectionable content or leaking information, eroding customer trust and confidence.
3.2. Business impacts
Successful brute force attacks yield profound and enduring effects:
- Direct financial losses: Funds stolen, remediation costs, customer compensation, and legal fees, especially with sensitive data exposure.
- Data loss and information leaks: Exposed customer or internal data leads to business setbacks and regulatory risks, such as fines under data protection laws.
- Operational disruptions and performance degradation: Compromised systems require shutdowns, causing downtime, revenue loss, and poor user experiences.
- Long-term reputational harm: A single data breach or defaced website erodes customer loyalty, with recovery demanding substantial time and resources.
- Heightened risk of follow-on attacks: Initial breaches facilitate ransomware, lateral movement, and escalated damage.
.jpg)
4. Tools commonly used by hackers for brute force
To execute large-scale, rapid brute force operations, attackers rely on specialized automation tools. Notable examples include John the Ripper, Hydra, Aircrack-ng, and Hashcat, which also serve legitimate penetration testing but become potent weapons when misused.
- John the Ripper: Open-source tool for cracking passwords across various platforms (Windows, Unix, macOS).
- Hydra: Supports password testing on multiple protocols (HTTP, FTP, SSH, Telnet).
- Aircrack-ng: Focuses on Wi-Fi attacks by decrypting packets to recover WPA/WPA2 keys.
- Hashcat: Harnesses GPU acceleration for billions of attempts per second.
These tools are valid in penetration testing but transform into dangerous instruments in adversarial hands.
5. Effective brute force attack prevention strategies
While completely eliminating brute force risks is challenging, proper defenses significantly mitigate threats. The following proven approaches strengthen protections for accounts and systems.
5.1. Enforce strong password policies
- Passwords must be at least 10 characters, incorporating uppercase and lowercase letters, numbers, and special characters.
- Avoid predictable sequences like names, birthdates, or common words.
- Adopt passphrases, such as "Hanoi$Autumn2025!", to enhance unpredictability.
5.2. Limit failed login attempts
Restrict accounts after 3 to 5 incorrect tries with temporary lockouts to thwart automated attacks. Pair this with email or SMS alerts for suspicious activity.
5.3. Implement CAPTCHA and multi-factor authentication (MFA)
CAPTCHA blocks automated bots, while MFA adds verification via phone or email before granting access.
5.4. Encrypt and salt passwords
Store passwords as salted hashes to prevent decryption even if databases are compromised.
5.5. Monitor anomalous login behavior
Detect patterns like logins from unfamiliar IPs or mass failed attempts for early warnings.
5.6. Regularly update and patch vulnerabilities
Maintain administrative software, CMS, and plugins with timely updates to close exploitation paths.
6. Brute force and its connection to DDoS
Brute force attacks often coincide with DDoS, particularly at the application layer (Layer 7). The goal is resource exhaustion, slowing servers and providing more time for password trials.
At VNETWORK, brute force falls under advanced application layer attacks, requiring multi-layer defense solutions like VNIS for real-time detection and mitigation.
7. VNIS: Comprehensive shield against brute force and DDoS for enterprises
VNIS (VNETWORK Internet Security) is an AI-driven security platform developed by VNETWORK, engineered for early detection, rapid response, and automated defense against sophisticated threats including brute force, botnets, and DDoS.
The system leverages real-time behavioral AI to identify anomalies in milliseconds and preemptively neutralize attacks.
.png)
VNIS delivers proactive brute force defense:
Within the Cloud WAAP layer, VNIS features Account Takeover Prevention (ATP) to halt account takeover attempts, including brute force, at the earliest stages. Integrated with AI and machine learning, ATP provides proactive enterprise protection while preserving user experience:
- Suspicious access detection: Automatically scans and addresses abnormal behaviors, focusing on high-risk accounts.
- Flexible ATP rules: Activates context-aware custom protections to block brute force efforts promptly.
- WAF and AI integration: Enables instant responses to attacks without disrupting legitimate users.
These capabilities position VNIS as a proactive shield, enabling Vietnamese enterprises to secure user accounts and maintain operational stability against modern brute force threats.
8. Conclusion
Though not novel, brute force endures as one of the most dangerous and widespread attack techniques today. Amid evolving cybercrime sophistication, enterprises cannot rely solely on traditional firewalls; they require multi-layered, intelligent, self-learning solutions like VNIS.
With VNIS, businesses gain protection from brute force and DDoS while ensuring stable performance, security, and sustainable growth in the digital landscape.
FAQ: Common questions about brute force
1. What is brute force?
Brute force is a cyberattack where hackers test numerous username and password combinations until success. It exhaustively seeks unauthorized system access.
2. How dangerous is a brute force attack?
Brute force enables system access, customer data theft, malware installation, or website control, resulting in major financial and reputational harm to businesses.
3. How to detect a brute force attack on a system?
Indicators include repeated failed logins from multiple IPs, sudden traffic spikes, logs showing hundreds of requests per minute, or server anomaly alerts.
4. How can enterprises prevent brute force?
Employ multi-factor authentication (MFA), failed login limits, CAPTCHA, real-time monitoring, and WAAP solutions like VNIS for automated detection and blocking.
5. How does VNETWORK's VNIS counter brute force?
VNIS integrates AI, machine learning, and global Multi-CDN to identify attack behaviors, block brute force at Layer 7, and sustain system performance during large-scale incidents.
