1. What is DKIM?
DKIM (DomainKeys Identified Mail) is an email authentication protocol that allows the receiving mail server to verify:
- Whether the email was genuinely sent from the declared domain
- Whether the email content was altered during transmission
DKIM uses a public key and private key cryptographic mechanism to digitally sign outgoing emails. The receiving server validates this signature using the sender domain’s DNS record.
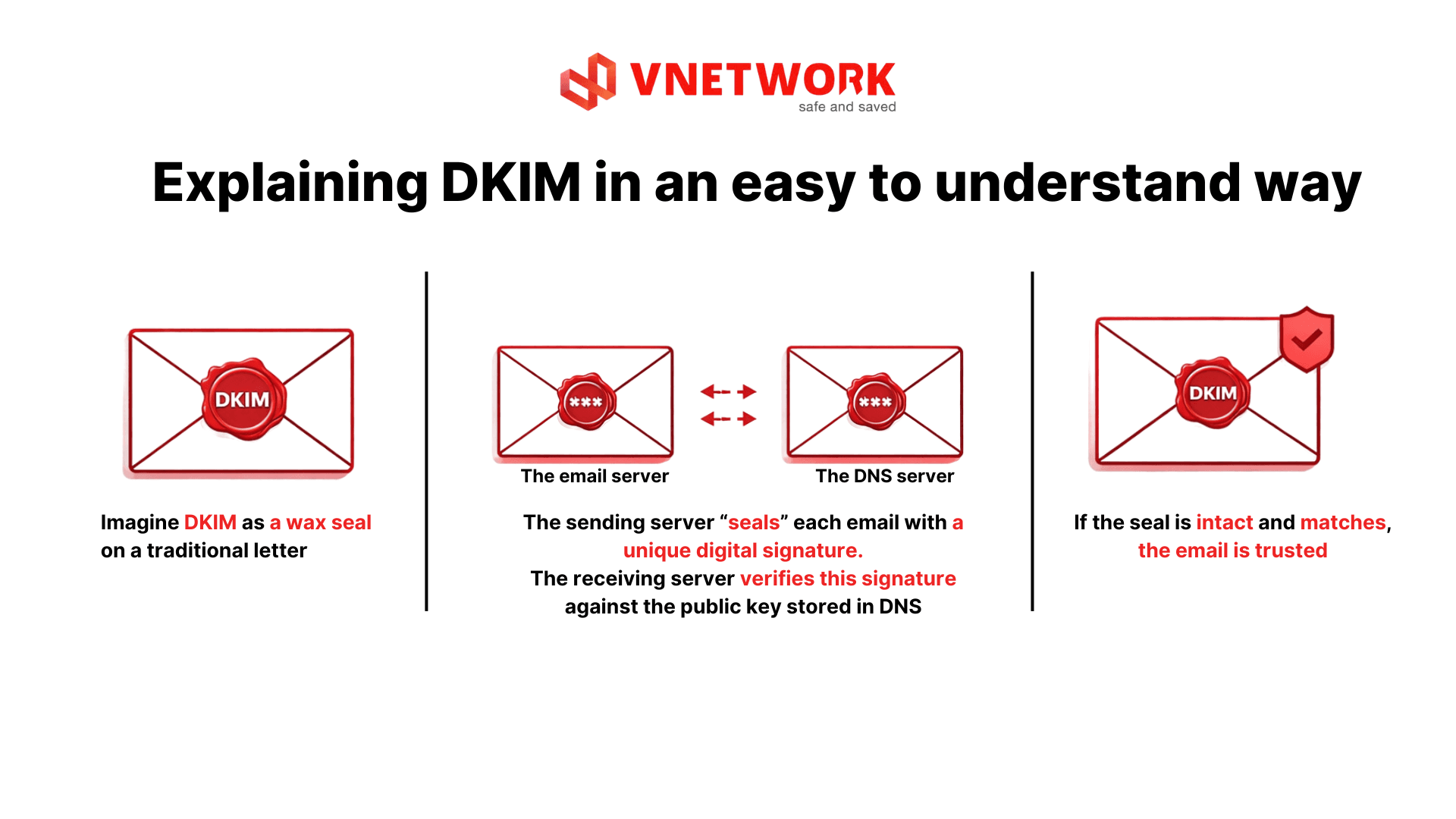
Simply put, DKIM acts as a digital seal that verifies the identity of an email, enabling receiving systems to distinguish legitimate messages from spoofed ones.
2. How does DKIM work?
To understand how DKIM authenticates email and prevents spoofing, it is important to look at how the mechanism operates in practice. At its core, DKIM relies on digital signatures to help the receiving server validate the sender’s identity and ensure message integrity during transit.
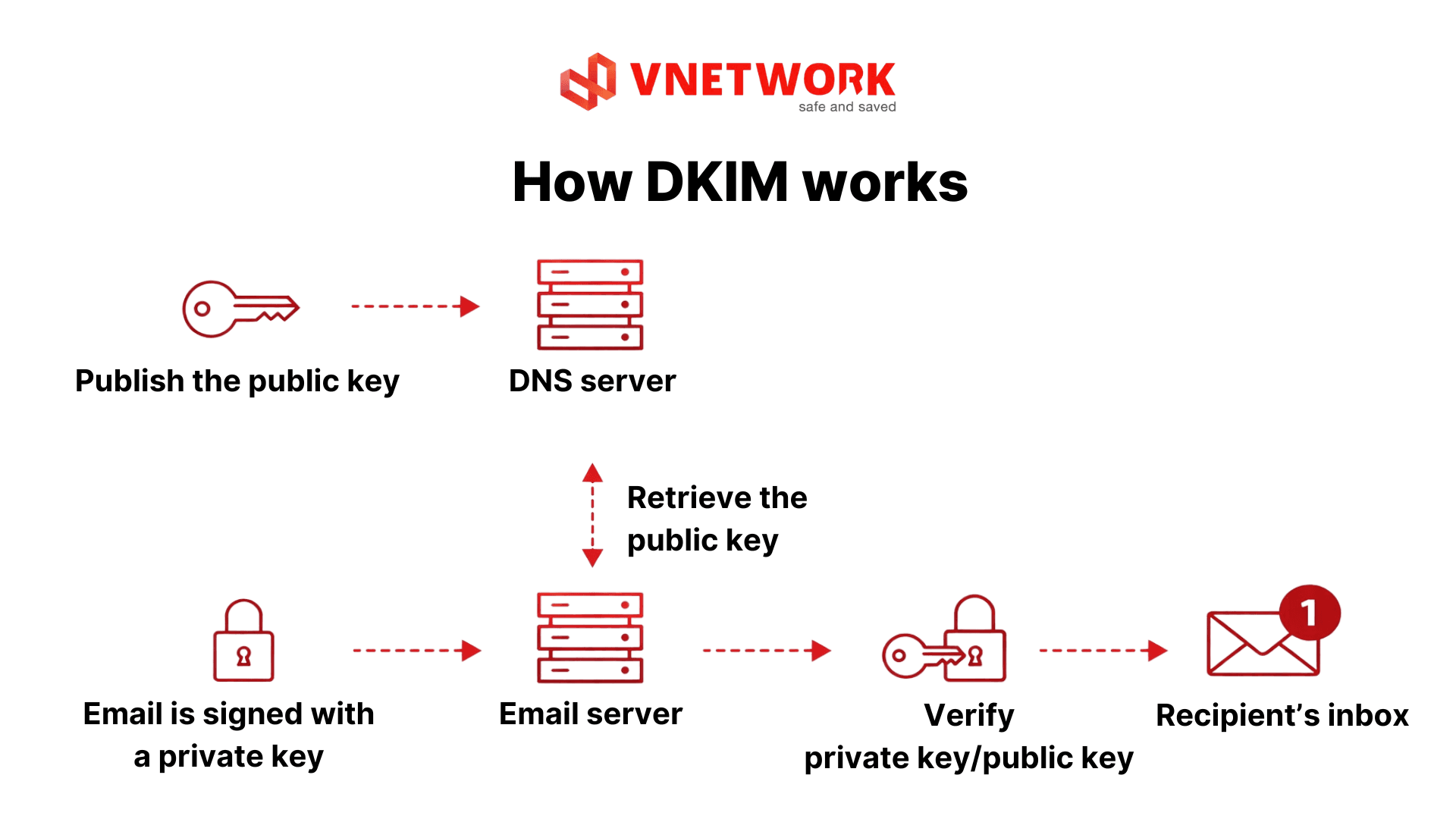
The DKIM authentication process is fully automated and consists of four main steps:
2.1. DKIM key pair generation
The domain owner generates a cryptographic key pair that includes:
- Private key: securely stored on the outbound mail server and never shared externally
- Public key: published in the domain’s DNS records
This public key is associated with a DKIM selector, which allows the receiving server to identify which sending system within the same domain signed the email.
2.2. Signing the email before sending
Before an email is sent, the mail system generates a unique authentication signature based on the email content and sender information.
This signature:
- Is unique for each email
- Is created using the domain’s private key
- Is embedded into the email’s technical headers
As a result, every outgoing email carries a digital “signature” that proves the identity of the sending domain.
2.3. Signature verification by the receiving server
When the email reaches the recipient’s mailbox, the receiving server will:
- Retrieve the sender domain’s public key from DNS
- Use that key to validate the DKIM signature included in the email
- Compare the signature against the received message content
This process allows the receiving system to determine whether the email genuinely originated from the stated domain and whether the content was modified in transit.
2.4. DKIM authentication result
- If the signature is valid and the content remains intact, the email passes DKIM authentication
- If the signature is invalid or the content has been altered, the email may be marked as spam or rejected
The entire verification process occurs within milliseconds and has no impact on the end user experience.
3. Why is DKIM important for enterprises?
As email continues to be a primary attack vector for impersonation and fraud, enterprises can no longer rely solely on the visible sender address to assess trustworthiness. DKIM has become a foundational authentication standard that enables organizations to control sending identity and strengthen email security.
Specifically, DKIM delivers value to enterprises in the following areas:
- Prevents email spoofing: DKIM verifies that emails are genuinely sent from authorized domains, reducing the risk of attackers impersonating brands to deceive customers, partners, or internal staff.
- Improves inbox delivery rates: Major email providers such as Google, Microsoft, and Yahoo treat DKIM as a key trust signal. Emails without DKIM or with misconfigured DKIM are far more likely to be routed to spam folders.
- Serves as the foundation for DMARC deployment: DMARC relies on DKIM or SPF to function effectively. In practice, DKIM plays a critical role in enabling enterprises to enforce DMARC policies and protect their email domains.
In summary, DKIM not only helps prevent email spoofing but also directly improves email deliverability and serves as a prerequisite for advanced email authentication standards such as DMARC. For enterprises, DKIM is an essential component of any professional email security and domain protection strategy.
4. What is a DKIM selector?
During DKIM deployment and day to day operations, enterprises will frequently encounter four key concepts: DKIM selector, DKIM record, DKIM check, and DKIM test. Each component serves a different purpose, yet they are tightly connected within the email authentication and control process.
First, a DKIM selector is a string that identifies which DKIM key is used to sign an email when a domain has multiple DKIM keys.
Example:
selector1._domainkey.tenmiencuaban.vn
The selector enables receiving systems to identify which sending system signed the email, while also allowing organizations to manage multiple email sending sources under the same domain.
The role of a DKIM selector:
- Allows a single domain to use multiple DKIM keys
- Enables each email sending system to use its own selector
- Supports periodic key rotation to enhance security
5. What is a DKIM record?
A DKIM record is a TXT record in the domain’s DNS that contains the public key used by the receiving mail server to verify the DKIM signature of an email.
Example DKIM record:
v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQ...
When an email is received, the mail server queries the DKIM record associated with the selector to validate the DKIM signature.
6. What is DKIM check?
DKIM check refers to the process of verifying the status and validity of DKIM, including:
- Whether the domain has a DKIM record configured
- Whether the DKIM record structure is correct and valid
- Whether outgoing emails successfully pass DKIM authentication
DKIM check is commonly performed by:
- Inspecting DNS records
- Analyzing the technical email headers
7. What is DKIM test?
DKIM test involves sending test emails to evaluate whether DKIM functions correctly in real world conditions before official use.
DKIM test helps enterprises:
- Confirm that DKIM is working as configured
- Verify compatibility with SPF and DMARC
- Detect configuration issues early before large scale email campaigns
To clearly illustrate the differences and relationships between these concepts, the following summary outlines the role and purpose of each DKIM component.:
| Ordinal number | Ingredient | Nature | Primary purpose | When used |
| 1 | DKIM selector | Identifier string for a DKIM key | Distinguish multiple DKIM keys on the same domain | During configuration and sender management |
| 2 | DKIM record | TXT record in DNS | Provide the public key for email authentication | During DKIM deployment |
| 3 | DKIM check | DKIM status verification | Assess whether DKIM is valid and correctly configured | During audits and troubleshooting |
| 4 | DKIM test | Test email sending | Validate DKIM behavior in real sending scenarios | Before sending bulk or production emails |
It is clear that DKIM selector, DKIM record, DKIM check, and DKIM test do not operate independently. They work together throughout the entire DKIM authentication lifecycle. Understanding the role of each component enables enterprises to deploy DKIM effectively, maintain control over email sending sources, and minimize configuration related risks during ongoing operations.
8. Comparing DKIM, SPF, and DMARC in email authentication systems
In modern email security, no single standard is effective on its own. DKIM is only one of three core pillars of email authentication. To truly protect a domain from spoofing, phishing, and inbox placement issues, enterprises must deploy SPF, DKIM, and DMARC together.
Each standard plays a distinct role in verifying sender identity and ensuring email integrity.
| Ordinal number | Criterion | What it authenticates | How it works | Primary role | Limitations |
| 1 | SPF (Sender Policy Framework) | Sending IP address | Checks whether the sending IP is authorized in DNS | Defines who is allowed to send email on behalf of the domain | Prone to issues with email forwarding and does not validate content |
| 2 | DKIM (DomainKeys Identified Mail) | Email content and signing domain | Uses a public key and private key pair to sign emails | Ensures message integrity and confirms the sending domain | Does not define enforcement actions when authentication fails |
| 3 | DMARC (Domain-based Message Authentication, Reporting and Conformance) | Domain alignment and authentication results | Combines SPF and DKIM to enforce policy decisions | Defines how failed emails are handled and provides reporting | Requires accurate configuration and proper SPF and DKIM alignment |
Together, SPF, DKIM, and DMARC form the foundation of modern email security. SPF controls who can send email, DKIM provides cryptographic proof of message integrity, and DMARC ties everything together through policy enforcement and visibility. Deploying all three is a fundamental requirement for protecting domain reputation, improving inbox placement, and reducing the risk of email based attacks.
9. Limitations of DKIM when deployed in isolation
DKIM represents a significant step forward in email authentication. However, DKIM is not a comprehensive email security solution when operating on its own. In practice, enterprises that rely solely on DKIM can still become victims of phishing, domain spoofing, and email abuse without realizing it.
The root cause lies in the fact that DKIM only verifies message integrity and the signing domain. It does not fully validate the visible sender identity that recipients see.
- Does not guarantee the validity of the “From” address: DKIM confirms that an email is signed by a legitimate domain and has not been modified, but it does not require the signing domain to match the domain displayed in the “From” field. As a result, attackers can spoof a brand in the sender address while the email still passes DKIM validation.
- Vulnerable to misuse due to lack of domain alignment: Phishing emails may carry a valid DKIM signature that belongs to a different domain than the one shown to the recipient. Because DKIM does not verify this relationship, mail servers struggle to reject such messages, and users are more likely to trust them.
- Risk exposure if the DKIM private key is compromised: If a DKIM private key is leaked or taken over, attackers can legitimately sign emails on behalf of the domain. In this scenario, spoofed emails continue to pass DKIM checks, creating a false sense of security.
- No requirement to originate from the domain’s mail infrastructure: DKIM signatures do not need to be generated by mail servers controlled by the domain owner. As long as a valid key is available, emails can be sent from anywhere, making it difficult for enterprises to control unauthorized sending sources.
- Insufficient protection against phishing and targeted attacks: DKIM does not enforce any policy when authentication fails. As a result, DKIM alone cannot stop domain spoofing, phishing, or unauthorized third party email sending.
DKIM is a necessary condition, but it is not sufficient for modern email security. Without being deployed alongside SPF and governed by DMARC policies, DKIM can create an illusion of safety while attacks continue unnoticed. Only when DKIM is part of a holistic authentication framework can enterprises truly protect their domains and email reputation.
10. DKIM application in business practice
In modern enterprise email environments, DKIM is more than a technical configuration. It serves as the foundation of an email authentication strategy and brand protection framework.
The following real world scenarios illustrate how DKIM is applied in common enterprise use cases.
- Enterprise scale email authentication strategy: In large organizations, email is often sent from multiple systems, increasing the risk of domain spoofing if not centrally managed. DKIM standardizes authentication by ensuring that all emails are digitally signed with the corporate domain. When combined with DMARC, it forms a scalable and effective enterprise email authentication foundation.
- Preventing executive impersonation attacks (Spear Phishing): Spear phishing attacks often impersonate senior executives to trick internal staff into performing sensitive actions. DKIM helps block emails that are not properly signed, and when DMARC is enforced, impersonation attempts are rejected at the receiving gateway.
- DKIM in email marketing and automation: Email marketing platforms frequently send messages on behalf of enterprises using brand domains. Configuring dedicated DKIM selectors for each platform ensures authentication success, maintains inbox placement, and enables precise control over sending sources.
- Managing DKIM at scale across regions and domains: With multiple domains, subdomains, and email providers, manual DKIM management becomes complex and error prone. Enterprises must centrally track DKIM key and selector lifecycles to ensure consistent alignment with SPF and DMARC.
- DKIM in a Zero Trust email model: In a Zero Trust approach, no email is trusted by default, even if it passes technical authentication. DKIM acts as the initial verification layer, providing the baseline for advanced security controls to further evaluate email behavior and context.
Across these scenarios, DKIM plays a central role in validating sending sources and protecting enterprise domains. When properly implemented and combined with appropriate control mechanisms, DKIM becomes a solid foundation for a secure and scalable email security architecture.
11. VNETWORK EG-Platform - From DKIM to multilayer email security
DKIM validates sending sources and ensures message integrity, but it only addresses part of the email security challenge. In real enterprise environments, modern threats such as spear phishing, targeted fraud, and internal data leakage require a more comprehensive approach.
EG-Platform implements email authentication standards including SPF, DKIM, and DMARC at the very first protection layer, SpamGUARD. At this layer, technical authentication is combined with Machine Learning and Bayesian filtering to assign a risk score to each email. This enables automatic filtering and blocking of spam, phishing, and emails containing malware or ransomware.
In practice, EG-Platform is designed to extend DKIM into a multilayer email security system. Instead of stopping at signature and DNS record checks, the platform integrates technical authentication with behavioral analysis and end to end control across both inbound and outbound email flows. This allows enterprises to proactively address modern email threats.
Key differentiators of EG-Platform include:
- Protection for both outbound and inbound email: While DKIM focuses on authentication at the receiving side, EG-Platform extends protection to outbound email through the SendGUARD layer. This helps prevent not only external spoofing but also internal data leakage, accidental exposure of sensitive information, and abuse of compromised internal accounts.
- Technical authentication combined with Machine Learning from the first layer: SPF, DKIM, and DMARC are enforced at the inbound defense layer (SpamGUARD), together with Machine Learning and statistical filtering. This approach enables automatic detection and blocking of spam, phishing, malware, and ransomware, even when emails appear technically valid.
- Behavioral and contextual analysis beyond signature validation: DKIM confirms that an email has not been altered and is signed by a valid domain, but it does not evaluate intent or content. EG-Platform adds a deep analysis layer (ReceiveGUARD) that inspects sending behavior, content context, links, and attachments in a secure environment. As a result, sophisticated attacks can still be detected even if emails pass DKIM, SPF, and DMARC.
- Compliance readiness for high security environments: EG-Platform is assessed against the ITU-T X.1236 framework of the International Telecommunication Union (ITU), a reference standard for the quality and effectiveness of email security solutions. This provides enterprises, especially in regulated sectors such as finance, government, and education, with a structured foundation for deploying and operating email security systems.
- Alignment with modern email security models: Rather than focusing solely on domain authentication, EG-Platform adopts a Zero Trust email model where no message is trusted by default. Every email is continuously evaluated based on technical authentication, behavior, and context, in line with modern email security practices recommended by international cybersecurity experts.
As a result, EG-Platform does more than support DKIM check or DKIM test tasks. It functions as a comprehensive email security platform. By combining technical authentication, behavioral analysis, and centralized management, EG-Platform enables enterprises to proactively protect their email systems against modern threats.
FAQ - Frequently asked questions about DKIM
1. Is DKIM mandatory for enterprises?
DKIM is not legally mandatory, but it is practically required from a technical perspective for protecting email reputation and effectively deploying DMARC.
2. How long does a DKIM check take?
DKIM checks are almost instantaneous. However, after adding a DKIM record, DNS propagation may require some time to complete globally.
3. Does DKIM test affect production email?
No. DKIM test uses test emails to validate configuration and does not impact official email sending operations.
4. Can a single domain use multiple DKIM selectors?
Yes. Using multiple DKIM selectors for different sending systems is recommended to improve security and simplify management.
5.How does EG-Platform support DKIM?
EG-Platform integrates DKIM within the SpamGUARD layer, combined with SPF, DMARC, and Machine Learning models to authenticate emails, assess risk, and detect anomalies. This significantly enhances email security compared to using DKIM alone.
