1. What is HTTP Flood? The relationship between HTTP Flood and DDoS
HTTP Flood represents a DDoS (Distributed Denial of Service) attack variant at the application layer (Layer 7), wherein adversaries flood the target server with a barrage of valid HTTP requests, typically GET or POST methods.
These requests mimic normal user behavior, complicating differentiation between genuine and malicious traffic. This leads to exhaustion of CPU, RAM, or bandwidth resources, resulting in website hangs or complete outages.
Unlike volumetric DDoS variants such as UDP Flood or ICMP Flood, HTTP Flood demands minimal traffic volume. Instead, it targets web application processing resources, earning its reputation as the most sophisticated and elusive attack vector.
.jpg)
As a branch of DDoS, HTTP Flood operates at the application layer, the interaction point between users and websites.
Traditional DDoS floods network bandwidth with fake traffic, whereas HTTP Flood depletes server processing capacity.
Attackers commonly harness botnets, networks of thousands of compromised devices including computers, IoT gadgets, IP cameras, and routers, orchestrated to dispatch synchronized HTTP queries.
The outcome disrupts service for legitimate users, causing operational interruptions, revenue declines, and reputational harm to businesses.
2. How HTTP Flood operates
Visualize a store with one salesperson overwhelmed by hundreds of fake customers asking endless questions without intent to buy. The employee cannot serve real patrons, mirroring how HTTP Flood congests web servers.
HTTP Flood manifests in two primary forms:
2.1. HTTP GET Flood
Attackers dispatch massive GET requests to static resources like images, CSS, JS, or HTML files, aiming to drain I/O resources, concurrent connections, and bandwidth. This slows websites, delays responses, or triggers full downtime.
Example: Continuously requesting a homepage banner image thousands of times, filling connection queues and degrading real user experiences.
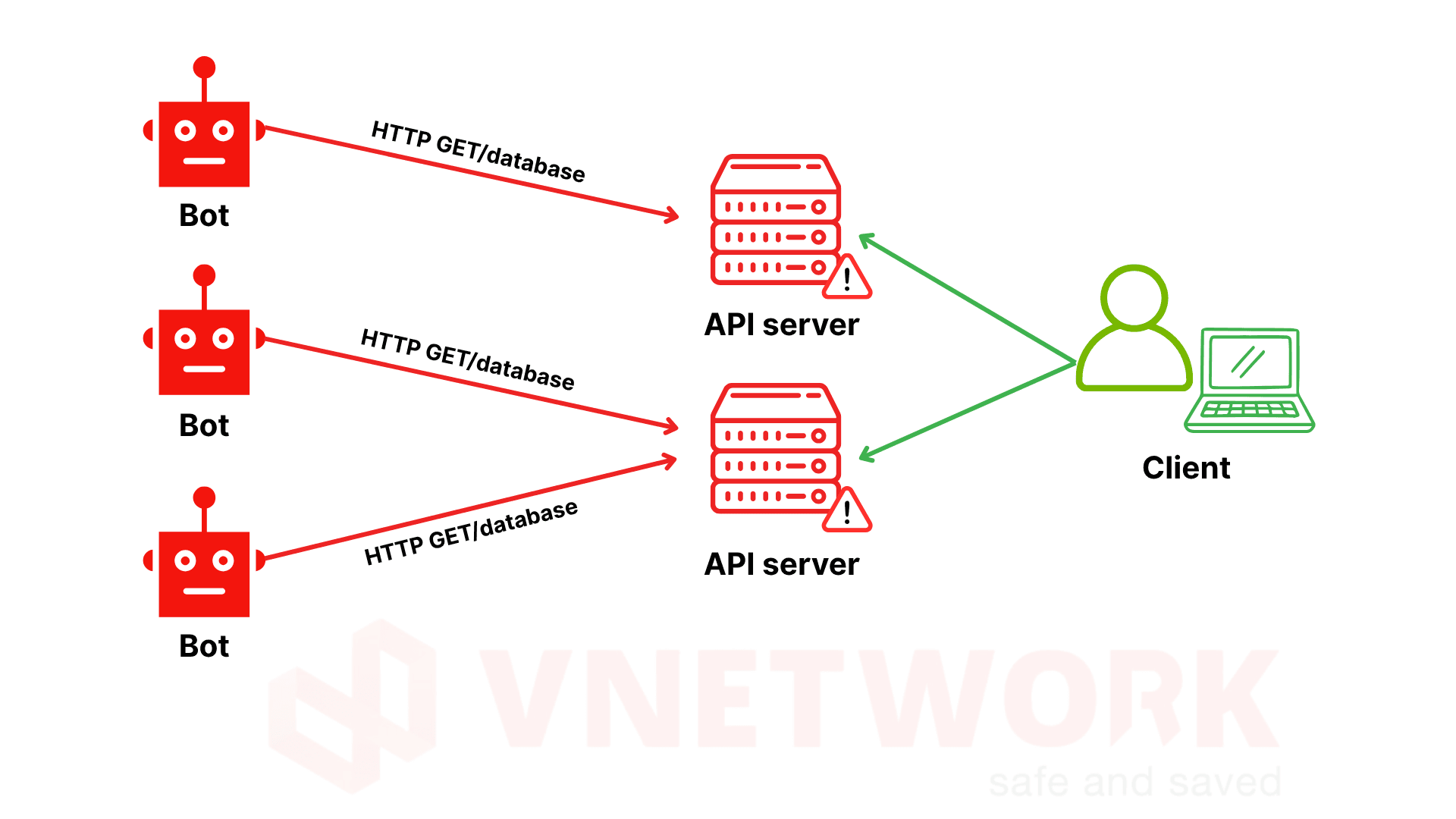
2.2. HTTP POST Flood
Attackers send voluminous POST requests to data-processing endpoints such as login, search, or payment forms, forcing the server to parse inputs, authenticate, query or write databases, and invoke internal services. This spikes CPU usage, occupies database connections, and bottlenecks application flows.
Example: Submitting thousands of fake login attempts with random payloads or targeting payment endpoints to trigger complex processing chains, leading to overload and system failures.
4. Why HTTP Flood evades detection
HTTP Flood easily bypasses defenses because attack requests technically resemble legitimate traffic, rendering conventional detection ineffective.
The following key reasons explain why HTTP Flood attacks silently consume resources and escape early security identification:
- Apparent legitimacy of requests: HTTP packets adhere to protocol standards, exhibit no formatting errors, and mirror valid user requests. They originate from diverse IP addresses with authentic User-Agent strings emulating browsers like Chrome, Firefox, or Safari. This obscures distinction between real and fake access.
- Limitations of standard filtering systems: Basic defenses including firewalls, IDS/IPS, or WAF relying on volume thresholds or signature matching often fail to detect these attacks, as traffic appears normal without clear patterns.
- Advanced obfuscation by attackers: Techniques include IP spoofing, header manipulation, frequency adjustments, or randomized timing to mimic natural behavior and evade scrutiny.
- Subtle yet severe impact: This realism allows HTTP Flood to quietly exhaust processing, bandwidth, and connections over hours until applications slow, services interrupt, or operations halt entirely.
5. Signs your website is under HTTP Flood
Businesses should suspect HTTP Flood victimization upon observing these indicators:
5.1. Abnormally slow website loading, especially dynamic pages
Server-side endpoints like login, search, or payment respond sluggishly or timeout. Static assets such as images or CSS may load via cache, indicating overload from dynamic requests. This directly impairs user experience and transaction completion.
5.2. CPU or RAM spikes without corresponding legitimate traffic
System resources surge while traffic analytics show no increase in valid users. This signals processing of fake requests that yield no business value, risking overall performance degradation.
5.3. Logs show repeated identical requests to the same URL from different IPs
Access logs reveal uniform patterns including identical URLs, parameters, or User-Agents across multiple IPs. This hallmark of botnets or automated scripts targets specific endpoints with relentless duplicate processing.
5.4. Real users report access failures or timeouts
Customer complaints about inability to reach the site or timeout errors provide tangible evidence of impacted experiences. Hanging pages, loading failures, or sluggish apps frustrate users and drive potential churn.
5.5. Monitoring tools repeatedly flag 503/504 errors
Frequent HTTP 503 (Service Unavailable) or 504 (Gateway Timeout) errors indicate servers or proxies cannot handle requests timely due to resource saturation. These common HTTP Flood outcomes disrupt services and harm enterprises.
Concurrent appearance of these signs strongly suggests an ongoing HTTP Flood against your website.
6. Severe impacts of HTTP Flood on businesses
HTTP Flood extends beyond technical disruptions to directly affect operations. It slows or halts websites, degrading user experiences, revenues, and brand reputation while escalating costs and risking critical data exposure.
- Revenue losses: Users cannot access sites, payment systems, or apps, resulting in abandoned transactions and direct financial shortfalls.
- Brand reputation damage: Prolonged downtime erodes user trust, satisfaction, and loyalty.
- Elevated remediation costs: Investments in infrastructure, bandwidth, or security experts rise to address incidents.
- Data exposure risks: Overloaded servers become vulnerable to exploitation, potentially leaking sensitive information.
- SEO penalties: Repeated downtime lowers search engine rankings, reducing traffic and business opportunities.
7. Effective HTTP Flood prevention methods
Completely stopping HTTP Flood proves impossible, but enterprises can minimize damage and enable early prevention through appropriate security measures.
7.1. Deploy Web Application Firewall (WAF)
WAF operates at the application layer to filter and block malicious requests before server impact. It detects anomalies like repeated accesses from single IPs, bot-driven requests, or HTTP Flood patterns. Legitimate user requests receive priority, mitigating service interruption risks.
7.2. Enhance load balancing
Load balancers distribute traffic across multiple servers, eliminating single points of failure. Overloaded servers trigger automatic redirection to alternatives, maintaining website, application, and API uptime during large-scale attacks.
7.3. Implement rate limiting
Cap maximum requests per IP within defined intervals to curb bot floods. This prevents server overload while preserving access for legitimate users.
7.4. User authenticity challenges (Challenge-based protection)
Integrate CAPTCHA, JavaScript challenges, or cookie validation to differentiate bots from humans. Suspicious patterns prompt additional verification, halting bots without affecting valid customers.
7.5. Real-time monitoring and alerting
Log analysis and behavior monitoring tools identify anomalous traffic instantly. Detected attack signs trigger immediate administrator alerts, enabling swift responses to limit damage and stabilize infrastructure.
8. VNIS: Comprehensive shield against HTTP Flood and Layer 7 DDoS
As HTTP Flood grows more sophisticated, enterprises require proactive, intelligent, and automated solutions. VNIS delivers exactly that: a full-stack security platform for web, apps, and APIs, developed by VNETWORK, Vietnam's leading comprehensive cybersecurity response center. How does VNIS safeguard businesses?
- Proactive AI-driven protection: VNIS employs artificial intelligence for prediction, identification, and real-time blocking of HTTP Flood and Layer 7 DDoS, ensuring websites, applications, and APIs remain secure against advanced threats.
- Robust global infrastructure: With 2,600 Tbps capacity and over 2,300 CDN PoPs, VNIS efficiently distributes traffic, sustaining stability amid massive attacks.
- Application-layer defense: Over 2,400 OWASP-standard WAF rules block common vulnerabilities like SQLi, XSS, and CSRF, combined with smart load balancing and origin shielding to optimize paths and offload origin servers, achieving 99.99% uptime.
- Instant monitoring and alerts: VNIS continuously tracks traffic, detects suspicious patterns, and issues immediate notifications for timely enterprise responses and risk reduction.
- Centralized, user-friendly management: Intuitive portal enables rapid feature toggling without deep expertise, integrating CDN, WAF, and DNS on one platform.
- 24/7 expert support: Backed by domestic and international security teams, AI, and automation, VNIS outperforms conventional solutions in defense capabilities, assuring system security and performance.
.png)
Thus, VNIS serves not only as a security shield but as an AI brain making websites smarter, safer, and more resilient against all network threats.
10. Conclusion
HTTP Flood ranks among the most sophisticated DDoS attacks, camouflaged within ordinary legitimate HTTP requests. Traditional security measures alone cannot protect enterprises from HTTP Flood without integrating artificial intelligence, globally distributed infrastructure, and professional SOC teams.
VNETWORK's VNIS provides the comprehensive solution meeting these three pillars: security, stability, and proactive response to all Layer 7 attack forms.
Empower your website, applications, and APIs with enhanced resilience today using VNIS, the leading AI-driven security platform in Vietnam and Asia.
FAQ: Common questions about HTTP Flood
1. How does HTTP Flood differ from traditional DDoS?
HTTP Flood is a Layer 7 DDoS variant using legitimate HTTP requests to overload servers, whereas traditional DDoS targets network layers (Layer 3/4).
2. Can small websites face HTTP Flood attacks?
Yes. Attackers often target small sites lacking advanced protections, making them easier to disrupt and harder to detect.
3. What are signs of an HTTP Flood on a website?
Slow loading, abnormal CPU spikes, logs with repeated requests from varied IPs, or frequent 503 errors.
4. How to prevent HTTP Flood?
Combine WAF, load balancers, rate limiting, and dedicated platforms like VNETWORK's VNIS for real-time anomaly detection and blocking.
5. Does VNIS protect against other Layer 7 attacks?
Yes. Beyond HTTP Flood, VNIS effectively counters SQL Injection, XSS, CSRF, API abuse, and various DDoS forms via integrated WAAP with artificial intelligence.
