What is the OSI Model?
In the modern world of computer networks, understanding how devices communicate with each other is essential. The OSI (Open Systems Interconnection) model serves as a common language, helping network engineers, programmers, and network security specialists discuss and solve technical problems effectively.
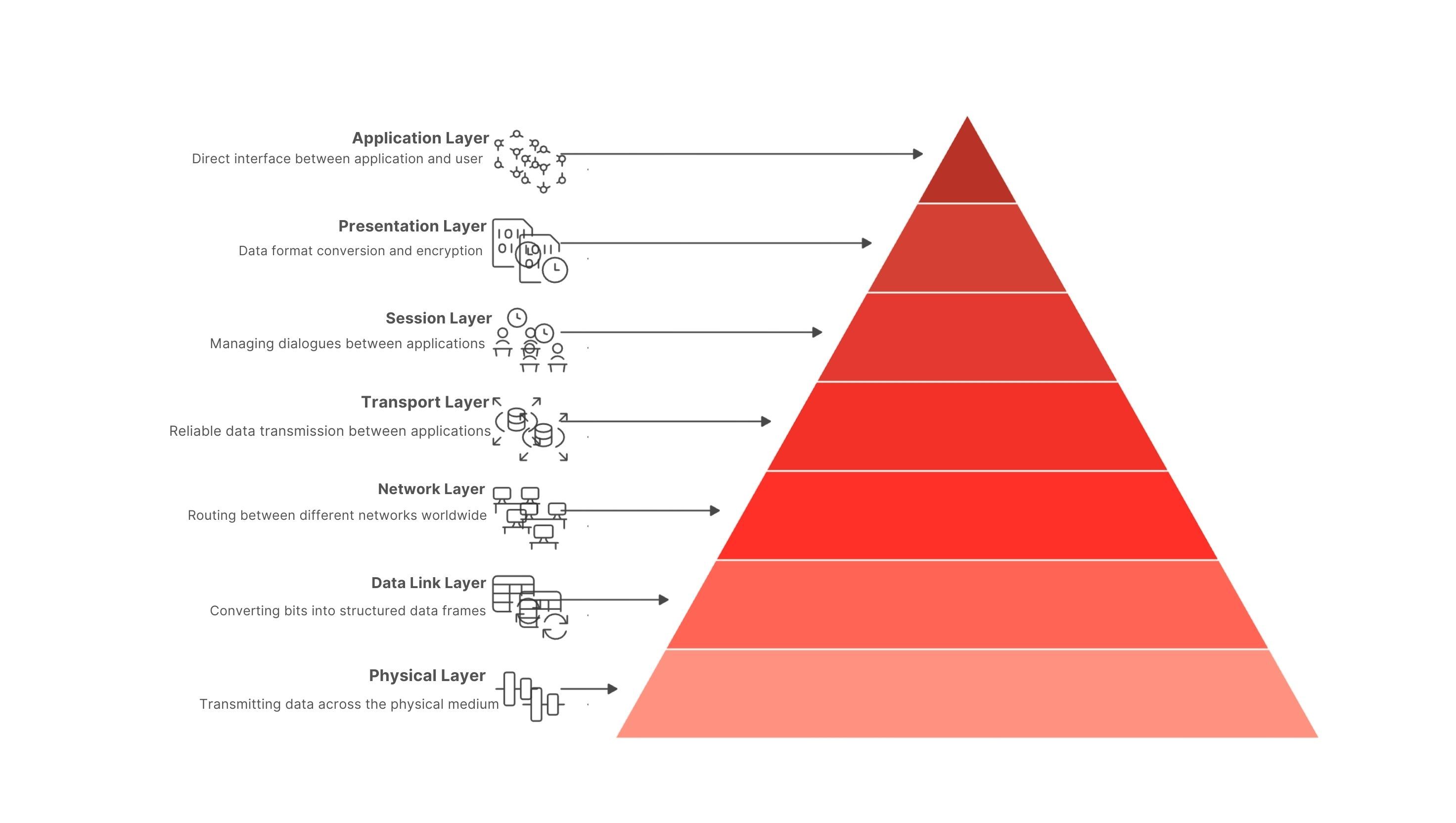
OSI is an international standard developed by the International Organization for Standardization (ISO), defining how different network systems can communicate with each other. This model divides the network communication process into 7 separate layers, each performing specific functions and interacting with adjacent layers.
Knowledge of the OSI model is not only a basic requirement for network certifications like CCNA, CompTIA Network+, but also an essential foundation for understanding network security, system administration, and network application development.
Concept and Development History of the OSI Model
The OSI model emerged in the late 1970s and was officially published in 1984, in the context where network equipment manufacturers developed products that were incompatible with each other. This situation caused major difficulties in connecting and integrating networks from multiple different vendors.
Main Objectives of the OSI Model
The OSI model was designed with three main objectives:
- First, to create a common standard for communication between computer systems from different manufacturers
- Second, to separate network functions into independent layers, making development and maintenance easier
- Finally, to provide a reference framework so technical professionals can discuss network issues in a unified manner
The Important Role of the OSI Model
The OSI model is an international standard framework developed by ISO. It describes how different network systems exchange data and interact with each other.
Its key feature is dividing the communication process into seven distinct layers, each with a clear function. This breakdown helps network engineers, developers, and security specialists easily visualize the entire process from the physical layer to the application layer.
The OSI model serves as a “common language” for the networking industry. This allows devices and software from different vendors to be compatible, creating a unified and flexible working environment.
It also plays a fundamental role in setting international standards, ensuring that systems worldwide operate in sync and can be connected and integrated seamlessly.
For network management and security, the OSI model is an effective tool for analysis and troubleshooting. Network professionals can quickly identify the layer where an issue occurs — from cable faults and routing errors to application malfunctions.
In education and training, the OSI model provides a clear learning structure. Students and newcomers can easily approach the topic and apply their knowledge directly to real-world tasks such as network design, security implementation, or troubleshooting.
Summary Table of the 7 OSI Model Layers
| Layer | Main Role | Example Protocols/Standards | Typical Devices |
| 7. Application | Service interface for applications/users | HTTP/HTTPS, DNS, SMTP, IMAP, FTP, Telnet | Web applications, mail clients |
| 6. Presentation | Encryption, compression, format conversion | TLS/SSL, JPEG, MPEG, ASCII/Unicode | Libraries in OS/applications |
| 5. Session | Establish/maintain/synchronize sessions | NetBIOS, RPC, PPTP* | System software |
| 4. Transport | End-to-end connection, error/flow control | TCP, UDP | Endpoints (servers, clients) |
| 3. Network | Logical addressing & inter-network routing | IP (IPv4/IPv6), ICMP, OSPF, BGP | Router, L3 switch |
| 2. Data Link | Frame packaging, MAC addressing, VLAN | Ethernet (MAC/LLC), PPP, 802.1Q, 802.1X | Switch, bridge, NIC |
| 1. Physical | Bit transmission over physical medium | UTP, fiber optic cables, 1000BASE-SX, RS-232 | Cables, hubs, repeaters, RJ-45 connectors |
Detailed Analysis of the 7 OSI Model Layers
Layer 1: Physical Layer
The physical layer is the foundation of the entire OSI model, responsible for transmitting data at the bit level through physical media. This layer does not care about the meaning of the data but only focuses on converting bits into physical signals and vice versa.
Main Functions: The physical layer defines the electrical, mechanical, and functional characteristics of the physical interface. This includes determining voltage levels to represent bit 0 and bit 1, data transmission speeds, as well as technical requirements for cables and connectors.
Standards and Protocols: Ethernet standards like 10BASE-T, 100BASE-TX, 1000BASE-T define how to transmit signals over copper cables. For fiber optic cables, there are standards like 1000BASE-SX and 1000BASE-LX. The RS-232 standard is used for traditional serial connections.
Operating Devices: Hubs are typical physical layer devices, operating as multi-port repeaters, amplifying and distributing signals. Repeaters extend transmission distance by regenerating signals. Network cable types like UTP, coaxial, and fiber optic cables also belong to this layer.
Real-world Example: When you connect a computer to a switch through an Ethernet cable, the physical layer ensures that electrical pulses carrying bit information are transmitted through 8 copper wires in the cable at the correct voltage levels (typically +/-2.5V) and speed (e.g., 100 Mbps).
Layer 2: Data Link Layer
The data link layer transforms raw bits from the physical layer into structured and meaningful data frames. This is the first layer that actually processes data instead of just transmitting it.
Main Functions: This layer performs three important functions. Framing organizes data into frames with headers containing source and destination MAC addresses. Error control is performed through checksum calculation and verification. Flow control ensures the sending device does not overwhelm the receiving device.
Typical Protocols: Ethernet is the most popular protocol, using 48-bit MAC addresses to identify devices. PPP (Point-to-Point Protocol) is used in dial-up connections and some broadband connection types. Wi-Fi uses the 802.11 standard with variants like 802.11n, 802.11ac.
Main Devices: Switches are the most characteristic devices of layer 2. Switches maintain a MAC address table, learn addresses of connected devices, and forward frames to the correct destination port instead of broadcasting like hubs.
Illustrative Example: In an office LAN, when computer A (MAC: aa:bb:cc:dd:ee:01) sends an email to computer B (MAC: aa:bb:cc:dd:ee:02), the switch will read the destination MAC address in the Ethernet frame and forward the frame only to the port connected to computer B, not to other computers.
Layer 3: Network Layer
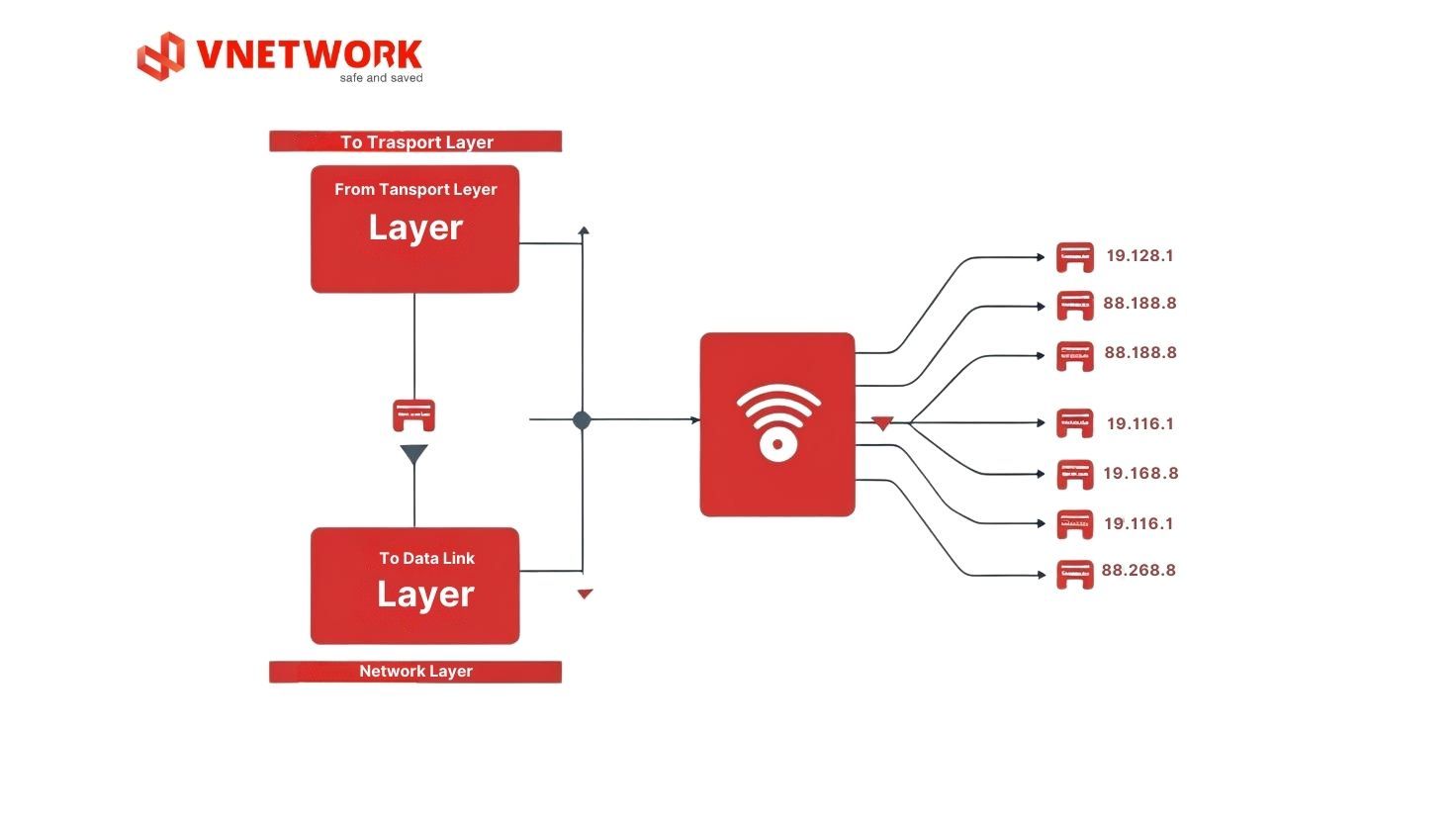
The network layer extends communication capability from local network scope to global by providing routing services between different networks. This is the first layer capable of logical addressing and routing.
Main Functions: Logical addressing through the IP address system allows unique identification of each device on the internet. Routing is the process of finding the optimal path from source to destination through multiple intermediate networks. Packet forwarding performs the sending of each packet along the chosen path.
Core Protocols: IPv4 uses 32-bit addresses (e.g., 192.168.1.1), while IPv6 uses 128-bit addresses to solve address exhaustion problems. ICMP provides network status information and is used by the ping command. Routing protocols like OSPF, BGP help routers exchange routing table information.
Specialized Devices: Routers are the main devices of layer 3, capable of connecting multiple different networks and deciding the path for each packet. Layer 3 switches combine switching and routing functions, commonly used in large internal networks.
Real-world Example: When you access Google from Vietnam, packets from your computer (IP: 192.168.1.100) will go through your home router (IP: 192.168.1.1), ISP router, multiple intermediate routers on the internet, and finally reach Google server (IP: 8.8.8.8). Each router reads the destination IP address and chooses the next optimal router.
Layer 4: Transport Layer
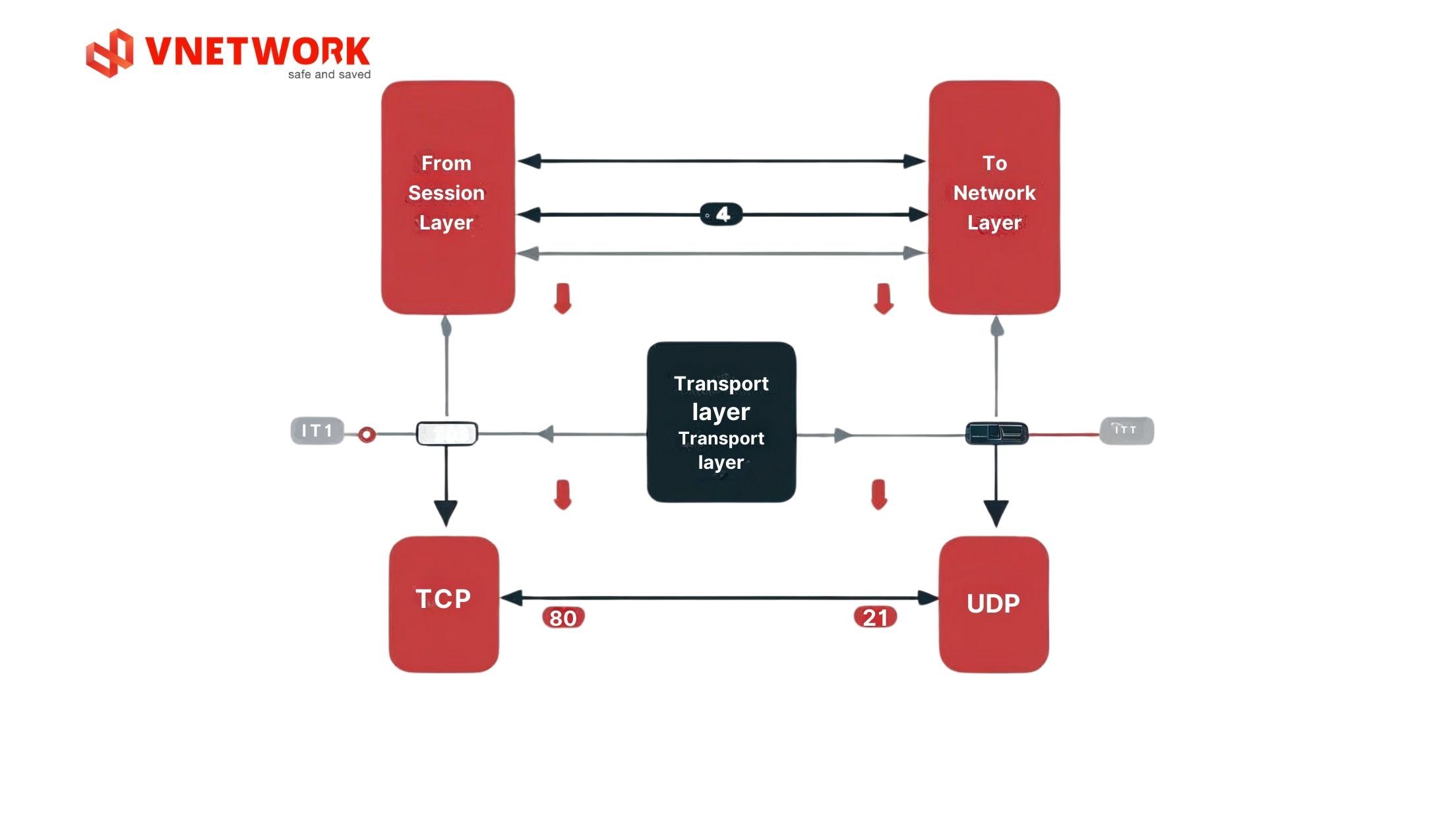
The transport layer ensures reliable data transmission between applications on two end devices. This is the first layer concerned with end-to-end data transmission rather than hop-by-hop.
Important Functions: Data segmentation divides large data into smaller segments for network transmission. Flow control adjusts data sending speed to avoid overwhelming the receiving device. Error control detects and requests retransmission of corrupted or lost data.
Main Protocols: TCP (Transmission Control Protocol) provides reliable connection with guaranteed data order and integrity through 3-way handshake mechanism and acknowledgment. UDP (User Datagram Protocol) prioritizes speed over reliability, suitable for real-time applications like video streaming.
Port Concept: Ports are identification numbers that allow multiple applications to use one network connection. Examples: HTTP uses port 80, HTTPS uses port 443, FTP uses port 21.
Illustrative Example: When downloading a 100MB file from the internet, TCP will divide the file into thousands of small segments, numbering each segment sequentially. If segment number 1500 is lost, TCP will detect and request retransmission of only that segment instead of the entire file. Conversely, when watching YouTube videos, UDP is preferred because losing a few video frames doesn't significantly affect the experience.
Layer 5: Session Layer
The session layer manages conversations (sessions) between applications on different computers. This layer ensures that data from different applications is not mixed up.
Main Functions: Session establishment includes authentication and negotiation of communication parameters. Dialog management controls data exchange, deciding when which application can send (half-duplex) or allowing simultaneous sending (full-duplex). Synchronization and recovery allows session restoration from checkpoints when errors occur.
Protocols and Services: NetBIOS (Network Basic Input/Output System) provides naming and session services for Windows networks. SQL sessions manage connections between applications and database servers. RPC (Remote Procedure Call) allows calling functions on remote computers like calling local functions.
Real-world Example: When using Microsoft Teams for online meetings, the session layer establishes and maintains the connection between your computer and Teams server. If the internet connection is interrupted for a few seconds, the session layer can automatically reconnect without requiring you to rejoin the meeting.
Layer 6: Presentation Layer
The presentation layer acts as an interpreter, converting data between different formats and performing encryption and data compression functions.
Main Functions: Converting data formats between different systems, for example from ASCII to EBCDIC or from little-endian to big-endian. Encrypting and decrypting data to ensure security during transmission. Compressing and decompressing data to reduce required bandwidth.
Standards and Protocols: SSL/TLS performs encryption for HTTPS, ensuring data is transmitted securely. JPEG, PNG, GIF are image compression standards. MPEG, AVI, MP4 are video formats. Compression algorithms like ZIP, RAR also operate at this layer.
Illustrative Example: When you access a bank website via HTTPS, the browser uses SSL/TLS at the presentation layer to encrypt login information before sending. When receiving responses from the server, this layer decrypts the data and displays the website. Similarly, when viewing JPEG images on the web, the presentation layer decompresses the JPEG format to display the original image.
Layer 7: Application Layer
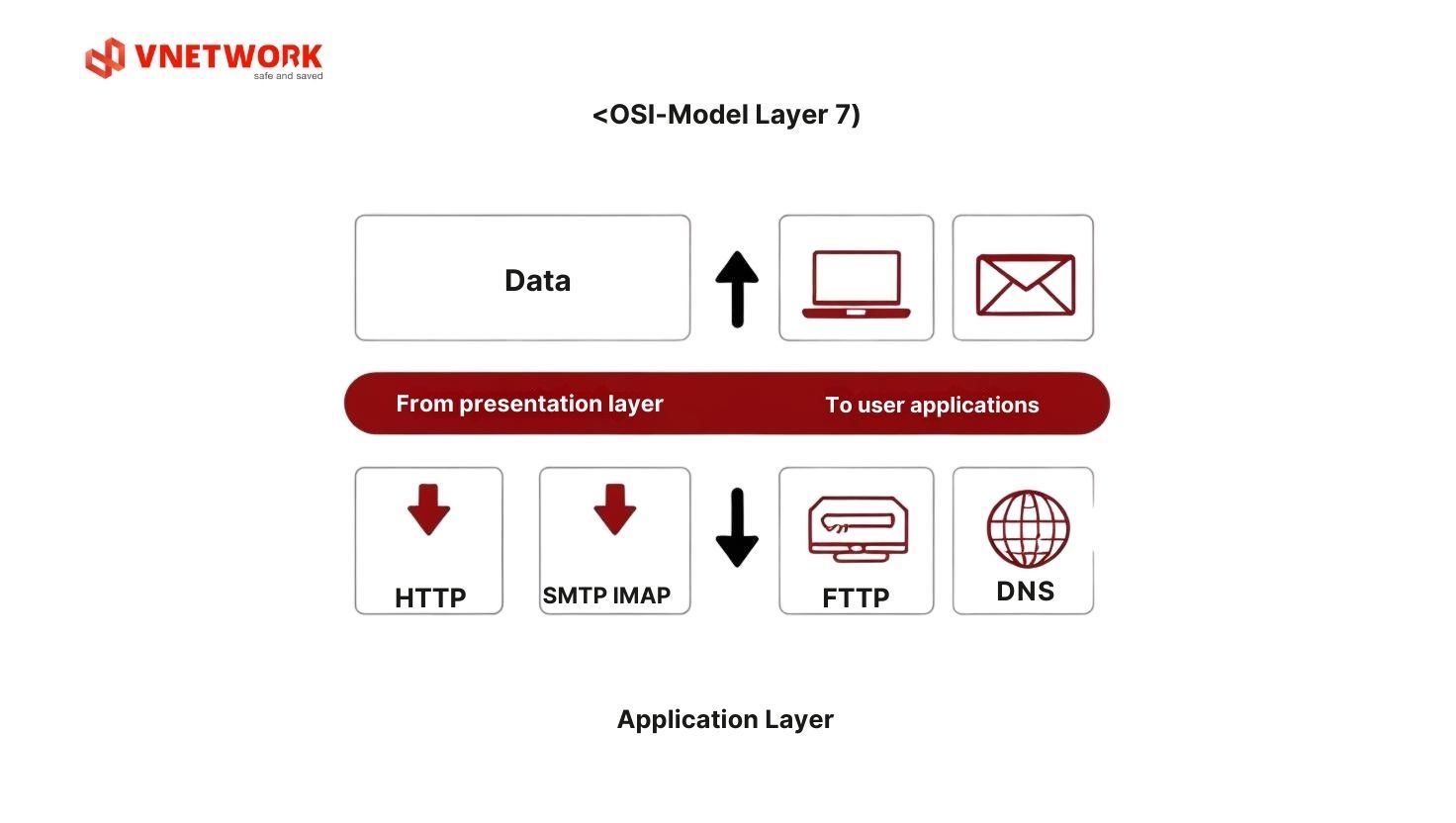
The application layer is the highest layer, providing direct interface between network applications and end users. This is the layer users frequently interact with.
Main Functions: Providing network services for user applications like web browsing, email, file transfer. Defining communication protocols between client and server. Handling issues like user authentication, checking resource access permissions.
Popular Protocols: HTTP/HTTPS is the foundation of the World Wide Web, with HTTP/2 and HTTP/3 bringing higher performance. SMTP sends email, POP3/IMAP receives email with IMAP allowing multi-device synchronization. FTP/SFTP transfers files with SFTP providing additional security. DNS resolves domain names to IP addresses. DHCP automatically assigns IP addresses to devices.
Real-world Example: When you type "facebook.com" into your browser, DNS resolver will convert the domain name to an IP address (e.g., 31.13.64.35). Then, the browser uses HTTPS protocol to send an HTTP GET request to Facebook server, receives HTML/CSS/JavaScript code and displays the website.
OSI and TCP/IP Models: Core Differences
The OSI (Open Systems Interconnection) model and TCP/IP (Transmission Control Protocol/Internet Protocol) model are the two most popular network architectures today. Both are used to describe how data is transmitted between devices in a network system. However, they differ in layer organization, application scope, and design goals.
| Comparison Criteria | OSI Model (7 layers) | TCP/IP Model (4 or 5 layers) |
| Number of layers | 7 layers: clear, separate functions | 4 or 5 layers, simplified for practical implementation |
| Design goal | Standardize communication for education, research | Designed to serve global Internet operations |
| Application scope | Theoretical, popular in education | Directly applied in real network systems |
| Application layer division | Application, Presentation, Session | Combines 3 above layers into Application |
| Popular protocols | HTTP, SMTP, TLS, TCP, IP, Ethernet... | HTTP, DNS, TCP, UDP, IP, Ethernet... |
| Layer detail level | High – beneficial for learning, modeling | Implementation-focused – convenient for system deployment |
| Suitable for purpose | Teaching, network certification, network troubleshooting | Real network design, programming and service deployment |
Advantages and Disadvantages of OSI Model
Advantages:
- Clear layering makes it easy to learn, remember, and analyze problems
- Suitable for teaching, research, network certification exams (CCNA, CompTIA...)
- Supports layered security thinking (defense-in-depth)
Disadvantages:
- Does not accurately reflect how protocols operate in real Internet applications
- Some layers like Session and Presentation are not clearly separated in modern applications
- Rarely used as a standard in practical implementation
Advantages and Disadvantages of TCP/IP Model
Advantages:
- Widely applied on the Internet and in practical network deployment
- Compact, simple structure, easy to integrate and develop
- Suitable for how modern protocols like HTTP, TLS, QUIC operate
Disadvantages:
- Lacks detail in some layers (no separate Presentation and Session)
- Less suitable for teaching purposes or in-depth layer error analysis
Frequently Asked Questions about OSI Model
Which Layer do Network Devices Operate at?
Switch: Most switches operate at layer 2 (Data Link), using MAC addresses to forward frames. Layer 3 switches can perform routing at layer 3.
Router: Mainly operates at layer 3 (Network), using IP addresses to route between different networks.
Hub: Operates at layer 1 (Physical), simply amplifying and distributing electrical signals.
Access Point: Operates at layer 2, similar to switches but for wireless connections.
Which Layer do Protocols Belong to?
- HTTP/HTTPS: Layer 7 (Application) - provides web browsing services
- TCP/UDP: Layer 4 (Transport) - manages end-to-end connections
- IP/ICMP: Layer 3 (Network) - performs routing and error notification
- Ethernet: Layer 2 (Data Link) - formats frames in LAN networks
Importance of OSI in Network Security
The OSI model provides a framework to analyze security threats at each layer. DDoS attacks can target layer 3 (IP flooding), layer 4 (SYN flooding), or layer 7 (HTTP flooding). Understanding this helps design effective multi-layered defense systems.
Conclusion
The OSI model with its 7 clear layers remains an important tool for understanding the nature of computer network operations. From transmitting bits through cables at the Physical layer to displaying web pages at the Application layer, each layer plays an irreplaceable role in a comprehensive network system.
Knowledge of the OSI model not only supports learning and certification, but is also a practical foundation for designing, implementing, and operating network systems. In the context of rapidly developing technology with cloud computing, IoT, and 5G, mastering the fundamental principles of OSI helps IT professionals adapt and effectively apply new technologies.
To learn more about applying OSI knowledge in modern network security solutions and professional network services, organizations can refer to comprehensive solutions from reputable network service providers.