1. What Is Rate Limiting?
Rate limiting (also known as rate control) is a mechanism that restricts the number of requests a user, application, or IP address can send to a server within a specified time frame. If the threshold is exceeded, the system may throttle, temporarily block, or reject subsequent requests.
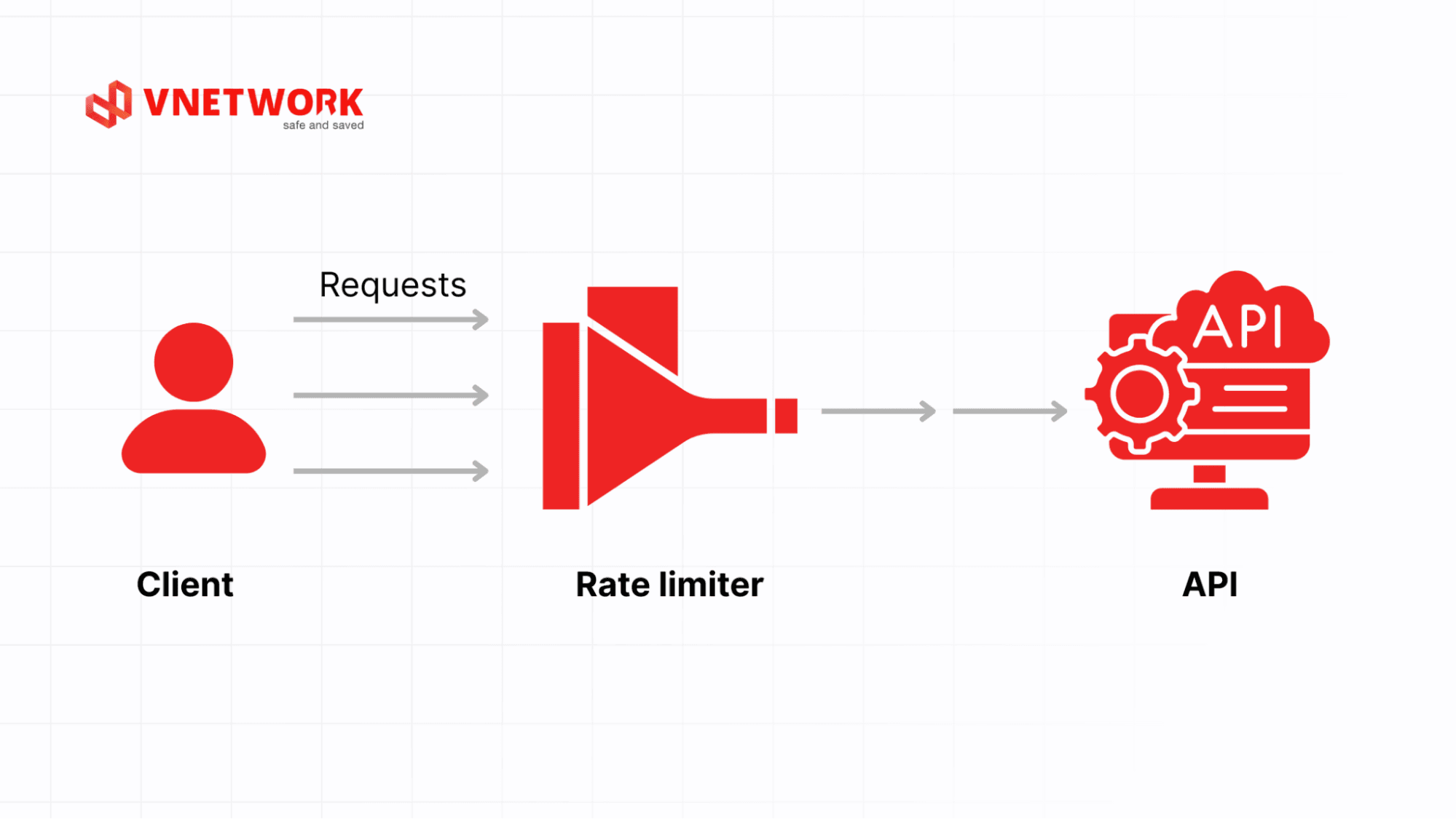
This mechanism helps achieve the following:
- Prevent users or bots from sending excessive requests in a short period
- Protect system resources
- Maintain stable performance
- Ensure legitimate requests are not congested
- Mitigate risks from bots, DDoS attacks, brute force attempts, and web scraping
Rate limiting is not merely a performance optimization technique; it is a cornerstone of modern cybersecurity strategies.
2. Why rate limiting is essential for security
Rate limiting goes beyond traffic management to form a foundational defense layer in contemporary web security. As cyberattacks grow more sophisticated and heavily automated, restricting request rates has become critical for protecting resources, blocking malicious bots, and ensuring uninterrupted operation of websites, applications, and APIs.
2.1. Mitigating DDoS risks
In a DDoS attack, adversaries flood servers with massive volumes of requests to exhaust resources. Rate limiting counters this by:
- Blocking IPs exhibiting abnormal request patterns
- Reducing load on web servers
- Preventing service outages
Distributed DDoS attacks using multiple IPs are harder to detect, but combining rate limiting with AI-driven solutions enables enterprises to identify anomalous patterns and respond intelligently.
2.2. Blocking brute force and credential stuffing attacks
Attackers deploy bots to test thousands of username/password combinations:
- Credential stuffing: Reusing leaked credential lists
- Brute force: Trying random or sequential passwords
Rate limiting caps consecutive attempts, detects high-density request spikes, and automatically imposes temporary lockouts on the offending source.
2.3. Preventing automated data scraping
Many e-commerce platforms suffer from competitor bots scraping pricing, product, or inventory data. Rate limiting helps by:
- Throttling abnormal request rates
- Rejecting rapid successive requests
- Detecting non-human behavioral patterns
This protects sensitive business data and preserves a consistent experience for genuine users.
2.4. Stopping inventory hoarding bots
Malicious bots add large quantities of items to carts without completing purchases, blocking real customers. Rate limiting identifies and blocks repetitive add-to-cart actions from bots, minimizing revenue loss and ensuring fair access to inventory.
3. How rate limiting works
Rate limiting is typically implemented within the application or API layer rather than solely at the web server. The process can be summarized as follows:
- Each incoming request is identified (via IP, API key, user session, etc.), and the system tracks the request count within a defined time window.
- The count is continuously compared against the configured threshold (e.g., 200 requests per minute).
- When the limit is exceeded, the system responds with actions such as throttling, temporary blocking, or returning the standard HTTP 429 Too Many Requests status.
In everyday terms, it works like a traffic officer slowing down speeding vehicles or a parent telling a child to eat more slowly when requests arrive “too fast” or “too many,” the system forces the client to slow down to protect shared resources.
4. Common types of rate limiting
4.1. User-Based rate limiting (Per User or IP)
The most widely used approach for APIs and web applications. Each user or IP is allowed a fixed number of requests in a given period. Exceeding the limit triggers temporary rejection—highly effective against brute force, credential stuffing, and server overload.
4.2. Geographic rate limiting
Enterprises can apply different thresholds based on the requester’s geographic region—for example, lowering limits for regions showing suspicious activity while raising them for primary markets. This balances security and user experience.
4.3. Server/Resource-Based rate limiting
Limits are enforced per server or resource pool to balance load and optimize performance. When paired with AI monitoring, thresholds can adjust dynamically according to real-time traffic and anomaly signals.
5. Popular rate limiting algorithms
5.1. Fixed-window
Requests are counted within fixed time intervals (e.g., 200 requests from 9:00:00 to 9:00:59). The counter resets at the start of each new window. Simple to implement but vulnerable to burst traffic at window boundaries.
5.2. Leaky bucket
Requests are processed from a queue at a constant rate, like water leaking from a bucket. Excess requests overflow and are dropped or delayed. Ideal for enforcing smooth, steady traffic flow.
5.3. Sliding-window (or Sliding-Window Log)
Combines the accuracy of fixed-window with smoothness by moving the time window forward with each request. It eliminates edge-of-window bursts and provides more consistent enforcement than the other two algorithms.
6. VNIS: AI-Powered comprehensive security with advanced rate limiting and bot protection
Today, bots generate over 50% of internet traffic. While traditional rate limiting handles basic abuse, sophisticated AI bots, rotating proxies, and human-like behavior require far more advanced defenses. This is where VNETWORK’s VNIS platform excels.
.jpg)
Superior global Infrastructure – The backbone of effective rate limiting
- More than 2,300 CDN PoPs across 146 countries
- 2,600 Tbps DDoS mitigation capacity
- Intelligent Load Balancing and Origin Shield
- 99.99% uptime guarantee
Abnormal traffic is identified and neutralized long before it reaches origin servers.
AI-Powered WAAP (Web Application & API Protection)
VNIS continuously updates over 2,400 OWASP-aligned WAF rules using global threat intelligence and real-time behavioral analysis. The AI engine automatically decides the best response: throttle, block, challenge with CAPTCHA, redirect, or observe in shadow mode.
Multi-Layer DDoS protection (L3/L4/L7)
While rate limiting primarily addresses application-layer abuse, VNIS extends protection across network, transport, and application layers, neutralizing threats such as HTTP floods, SYN floods, Slowloris, and TLS exhaustion.
Conclusion
Rate limiting remains a fundamental defense against bot-driven abuse and malicious traffic targeting web applications and APIs. However, as attackers deploy ever-more advanced bots, rotating proxies, and distributed attack infrastructure, traditional rate limiting alone is no longer sufficient.
VNETWORK’s VNIS platform, built from the ground up with AI at its core, delivers proactive, multi-layered protection that combines intelligent rate limiting, global CDN acceleration, advanced WAAP, and comprehensive DDoS mitigation. Ensuring both maximum security and optimal performance.
FAQ – Frequently Asked Questions
1. What is rate limiting?
Rate limiting restricts the number of requests a client can make to a server in a given time period to prevent congestion, protect resources, and mitigate bot and DDoS attacks.
2. How does rate limiting work?
It tracks request counts within a defined window. When the configured threshold is exceeded, the system throttles, blocks, or rejects additional requests, often returning HTTP 429 Too Many Requests.
3. Which rate limiting algorithm is best?
The sliding-window algorithm is generally considered the most accurate and flexible because it eliminates burst issues at window boundaries. The best choice ultimately depends on the specific use case and performance requirements.
4. Can rate limiting stop large-scale DDoS attacks?
Rate limiting effectively mitigates small to medium attacks and burst traffic, but it cannot fully stop large, distributed DDoS campaigns. Enterprises need dedicated multi-layer DDoS protection solutions such as VNIS for comprehensive defense.