What is Social Engineering?
Social Engineering refers to non technical attack techniques that exploit human psychology rather than technical vulnerabilities in systems. By taking advantage of trust, curiosity, greed, or fear, cybercriminals can trick victims into disclosing sensitive information, granting unauthorized access, or performing actions that cause damage.
In simpler terms, social engineering is the art of persuading people to open the door for attackers without directly hacking systems. Typical scenarios include receiving fake prize notification emails, phone calls impersonating banks, or malware infected USB drives left in public places.
Who are the most vulnerable targets?
In the workplace, anyone can become a victim of Social Engineering. However, certain roles are more frequently targeted due to their job functions and access levels.
- Receptionists and security staff: As the first point of contact, they often have access to employee schedules, basic internal information, and visitor details, making them attractive targets for information gathering.
- Office staff and managers: These roles often have access to important corporate data such as HR records, contracts, and project information, which increases their risk exposure.
- Executives and senior leaders: They hold highly sensitive information related to finance, business strategy, and growth plans. As a result, they face a particularly high risk of targeted Social Engineering attacks.
Identifying high risk groups allows organizations to implement appropriate security measures, reducing the likelihood of data breaches and financial losses.
Social Engineering attacks exploit human psychological factors to deceive victims. Attackers leverage trust and a sense of duty, greed or curiosity, as well as fear and lack of awareness, to manipulate users into disclosing sensitive information or performing risky actions.
Common Social Engineering techniques
Social Engineering relies on a wide range of sophisticated techniques to exploit human behavior and steal sensitive information. Understanding these common methods helps individuals and organizations defend more effectively.
- Phishing: Attackers send fraudulent emails or create fake websites impersonating trusted organizations such as banks, government agencies, or online services. The goal is to trick victims into entering credentials, passwords, or downloading malware. Phishing emails often create a sense of urgency, causing users to act without proper verification.
- Spear phishing: An advanced form of phishing that targets a specific individual or organization. Messages are customized based on personal details, job roles, and relationships, making them more convincing and harder to detect, significantly increasing the success rate of the attack.
- Baiting: Attackers use enticing bait to lure victims into downloading malware or connecting to compromised systems. Common examples include malware infected USB drives left in visible locations or attractive online ads promising gifts or special offers. Once the victim connects the device or downloads the content, malware is automatically installed.
- Vishing: Voice based scams conducted over phone calls, where attackers impersonate banks, government agencies, or colleagues to gain trust. Through persuasive conversation, they request account details, passwords, or one time verification codes, enabling access to personal and financial data.
- Piggybacking: Attackers exploit weak physical access controls by following authorized personnel into restricted areas or systems. This is often done by posing as employees, maintenance staff, or familiar contacts to avoid suspicion and gain access to sensitive information.
- Eavesdropping and hidden surveillance: Malicious actors deploy listening devices, hidden cameras, or spyware to collect sensitive information and monitor victim behavior. The collected data can then be used for further attacks, theft, or extortion.
- Fake pop ups: Attackers create deceptive pop up windows on browsers or applications, prompting users to enter personal information, download malware, or redirect to fake websites. These pop ups are often designed to resemble legitimate system or service notifications, making them difficult to distinguish for inattentive users.
Recognizing and understanding Social Engineering techniques is a critical step toward raising awareness and protecting systems, data, and personal information from increasingly sophisticated threats.
Risks of Social Engineering attacks
When targeted by Social Engineering, both individuals and organizations face serious risks. Understanding these threats helps improve vigilance and supports effective preventive measures.
- Data loss: Attackers can steal sensitive information such as business contracts, payroll data, customer records, or strategic plans. Data loss not only disrupts operations but also damages organizational credibility and competitiveness.
- Loss of privacy: Personal information of employees or customers may be exposed, leading to harassment, fraud, surveillance, or other illegal activities. Such incidents erode trust in the organization and negatively impact the personal reputation of those affected.
- Financial losses: Funds may be transferred from bank accounts without authorization, fraudulent transactions may occur, or goods may be redirected and stolen. Beyond direct financial damage, organizations often face additional legal and recovery costs.
- Business disruption: Corporate networks or websites may be compromised, resulting in system downtime, service interruptions, or loss of access to critical data. These disruptions impact business continuity, reduce revenue, and damage customer trust.
A clear understanding of Social Engineering risks enables individuals and organizations to proactively protect their assets, data, and privacy while maintaining secure and resilient business operations against evolving cyber threats.
How to prevent Social Engineering attacks
Preventing Social Engineering requires both individuals and organizations to stay vigilant and apply appropriate security measures. Proactive actions help reduce the risk of attacks and protect critical data.
For individuals
- Do not open emails, links, or attachments from unverified sources.
- Avoid reusing the same password across multiple accounts.
- Keep personal accounts separate from work accounts.
- Limit sharing schedules and personal information on social media.
- Stay calm and carefully verify any financial or payment related requests before taking action.
For organizations
- Implement multi factor authentication (Multi Factor Authentication).
- Define clear access controls and enforce strict account management.
- Use software to block spam, malware, and malicious pop ups.
- Regularly update security systems and antivirus solutions.
- Provide ongoing training for employees on Social Engineering and phishing risks.
Applying security measures at both the individual and organizational levels helps protect information, data, and critical assets from increasingly sophisticated Social Engineering attacks.
Why is email the most critical entry point?
Email is now the primary communication channel for businesses, handling around 90% of transactions, notifications, contracts, and internal data exchanges. For this reason, email has become the number one target for Social Engineering attacks.
According to statistics:
- 91% of ransomware attacks start with email.
- 90% of malicious emails contain no malware, allowing them to bypass traditional security systems.
- 65% of sensitive enterprise data is stored in email.
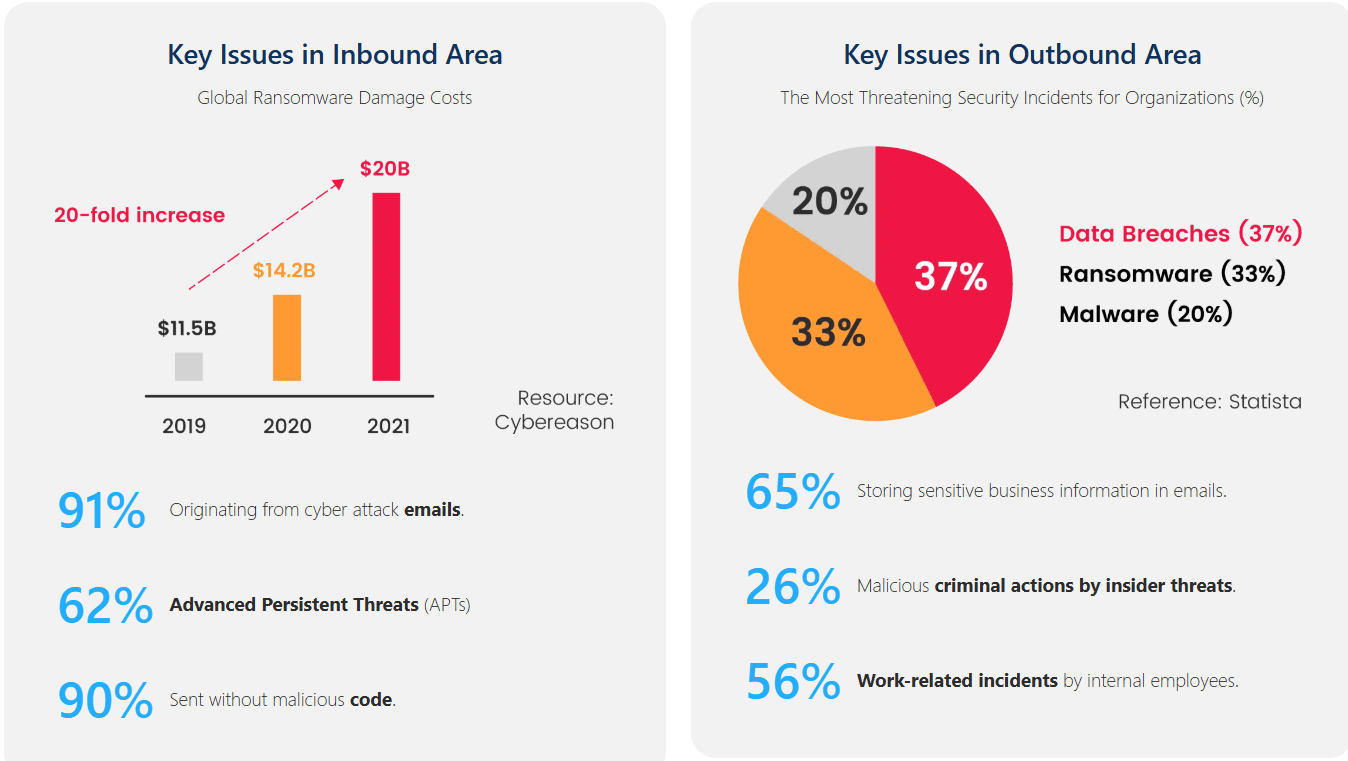
These figures show that standard email filtering solutions, including those from many large providers, are no longer sufficient to protect enterprises. As a result, there is a critical need for advanced email security solutions that follow international standards and can detect targeted attacks.
EG-Platform - An international standard AI powered email security solution against Social Engineering
EG-Platform by VNETWORK is the first email security solution in the world to fully comply with ITU-T X.1236 standards issued by the International Telecommunication Union (ITU). Built on Multi AI technology, a system that combines multiple AI models, EG-Platform is designed to:
- Analyze individual user email behavior.
- Detect anomalies before emails reach the inbox.
- Block 21 risk categories at the diagnostic stage.
- Prevent 17 types of inbound email attacks.
- Eliminate 12 types of outbound email threats.
Beyond protecting against common email threats, EG-Platform is specifically designed to counter Social Engineering attacks, which primarily exploit human psychology through spoofed, fraudulent, or manipulative emails. Below are three key protection layers.
- SpamGUARD - International standard spam and phishing filtering: SpamGUARD uses Machine Learning combined with Bayesian algorithms to analyze and assign risk scores to each email. At the same time, SPF, DKIM, and DMARC authentication mechanisms help identify and eliminate spoofed emails, stopping phishing attacks before they reach users.
- ReceiveGUARD - Blocking malicious emails before they reach the inbox: ReceiveGUARD inspects all attachments, links, and email content in a virtual environment (Virtual Area). Malicious links are converted into safe images, preventing users from accidentally accessing harmful content or falling victim to scams and malware infections.
- SendGUARD - Preventing internal data leakage: SendGUARD protects sensitive data by filtering critical keywords, requiring email approval before sending, blocking IP addresses from high risk countries, and offering password protected email delivery. This ensures that critical business information remains secure at all times.
With these three advanced protection layers, EG-Platform monitors the entire email lifecycle including sending, receiving, and content control. This comprehensive approach enables organizations to effectively defend against Social Engineering techniques such as phishing, spear phishing, spoofing, BEC (Business Email Compromise), and file or URL based baiting, significantly reducing risk and strengthening overall security posture.
FAQ - Frequently asked questions about Social Engineering
1. What is social engineering?
Social engineering is an attack technique that exploits human psychology to obtain information, gain unauthorized system access, or manipulate individuals into performing malicious actions without exploiting technical vulnerabilities.
2. How can phishing emails be identified?
Phishing emails often impersonate trusted organizations and create a sense of urgency. They typically include links or attachments that request personal information or prompt users to download software.
3. Who is most vulnerable to social engineering attacks?
Anyone can become a victim, especially office staff, senior managers, executives, or individuals with limited cybersecurity awareness.
4. What are effective measures to prevent social engineering?
Avoid opening suspicious emails or links, use multi factor authentication, enforce access control, keep security software updated, and provide regular employee training.
5. How does EG-Platform protect email?
EG-Platform leverages AI and Machine Learning to provide end to end email protection for inbound and outbound traffic. It blocks spam, phishing, malware, and targeted attacks in compliance with the international ITU-T X.1236 standard.
