What is Spear Phishing?
Spear phishing is a targeted form of phishing attack in which attackers do not send emails in bulk, but instead focus on a specific individual or a defined group within an organization.
Unlike traditional phishing, spear phishing emails are highly personalized and often impersonate people or organizations that the victim already trusts, such as:
- Company executives or direct managers
- Finance, accounting, or human resources departments
- Business partners or customers
- Familiar brands or service providers
.jpg)
Objectives of spear phishing
The ultimate goals of spear phishing attacks typically include:
- Stealing system credentials, email accounts, or VPN access
- Tricking victims into transferring money or committing financial fraud
- Distributing malware or ransomware
To achieve these goals, attackers rely heavily on social engineering techniques, exploiting trust, urgency, fear of penalties, or loss of access. In practice, human error remains the leading cause of security incidents and system downtime.
Real world example of spear phishing
A notable example is the spear phishing attack against Elara Caring, a home healthcare provider in the United States.
In December 2020, attackers specifically targeted two employees at Elara Caring through spear phishing emails. After successfully compromising their email accounts, the attackers illegally accessed personal data of more than 100,000 patients.
The exposed data included:
- Personal identification information
- Health insurance policy numbers
- Banking account details
- Medical records and other sensitive data
This incident demonstrates how a single successful spear phishing email can become the starting point of a large scale data breach, particularly dangerous in sensitive sectors such as healthcare and finance.
In addition, data from Tessian’s State of Email Security report in 2022 shows that email based attacks are not declining but increasing rapidly. According to the report, 94 percent of organizations experienced spear phishing or identity impersonation attacks, and 92 percent reported ransomware delivered via email. These figures confirm that email remains the most dangerous attack surface and the primary target for cybercriminals today.
Why Spear Phishing is especially dangerous
As security systems continue to improve, attackers are shifting away from large scale attacks and focusing instead on highly tailored emails designed for specific targets. Spear phishing exemplifies this trend, where a single human mistake can lead to severe consequences for an entire organization.
In reality, spear phishing is dangerous because only one successful email is enough for attackers to gain direct access to internal systems. Unlike purely technical attacks that require exploiting complex vulnerabilities, spear phishing directly targets user trust. Once a victim clicks a link or opens an attachment, attackers can quickly:
- Access sensitive enterprise data, including internal documents, project information, and system credentials
- Steal financial information and customer data, enabling fraud, scams, or illegal data trading
- Commit direct financial fraud, such as impersonating executives to request urgent wire transfers or changes in payment details
More critically, spear phishing often serves as the initial stage of advanced persistent threat attacks. After initial access, attackers do not immediately cause disruption. Instead, they remain hidden within the system for extended periods, gradually expanding access, monitoring data flows, and escalating privileges. These prolonged attacks are often detected only after organizations have suffered significant financial losses, operational disruption, and serious damage to brand reputation.
Differences between phishing and spear phishing
Email based impersonation attacks are becoming increasingly diverse and sophisticated. Among them, phishing, spear phishing, and whaling are the most common methods used to steal information or conduct financial fraud.
The fundamental difference between these three attack types lies in the target audience and the level of personalization.
| No. | Criteria | Phishing | Spear phishing | Whaling |
| 1 | Target | Mass distribution to large audiences | Specific individual or group | Senior executives such as CEO or CFO |
| 2 | Personalization level | Low and generic | Very high and context specific | Extremely high, exploiting authority |
| 3 | Sophistication | Medium | Highly sophisticated | Extremely sophisticated |
| 4 | Attack technique | Impersonation of common brands | Impersonation of colleagues or managers | Impersonation of partners or boards |
| 5 | Potential impact | Low to medium | High | Very high, often involving large sums |
- Phishing example: A mass sent email with the subject “Your bank account has an issue” asking users to click a link to reset their password, using generic content without personal details.
- Spear phishing example: An email sent specifically to an accounting employee, impersonating a direct manager, referencing a recent project and requesting an urgent transfer to a partner.
- Whaling example: An email impersonating a strategic partner or board member, sent directly to the CEO or CFO, requesting approval for a major financial transaction or access to confidential data.
In summary, while phishing relies on volume, spear phishing and especially whaling focus on target quality and deep personalization. This is what makes targeted attacks increasingly difficult to detect and a serious threat to enterprise email and financial security.
Why Spear Phishing is difficult to detect
In recent years, spear phishing emails have evolved far beyond crude and easily identifiable messages. Instead, they increasingly leverage new technologies and human weaknesses, driving higher success rates even in well secured organizations.
Modern spear phishing is particularly dangerous due to the following factors:
- Impersonation of trusted brands: Attackers often impersonate banks, digital signature platforms, delivery services, or familiar software vendors using realistic logos, email signatures, and content that closely resemble legitimate communications.
- Exploitation of internal trust: Emails are crafted to impersonate executives, HR, finance, or IT departments, referencing real projects or internal processes, exploiting employees’ trust and compliance mindset.
- Creation of urgency and psychological pressure: Messages such as “urgent transfer required” or “verify your account immediately” push recipients to act quickly without proper verification.
- Lack of employee security awareness training: Many organizations do not conduct regular email security training, leaving employees unprepared to identify sophisticated spear phishing attempts.
- Limitations of traditional email security systems: Signature based, keyword based, or blacklist driven email filters struggle to detect spear phishing because these emails often contain no obvious malware and change continuously.
- Use of generative AI: Attackers now use AI to write emails that sound natural, contextually accurate, and grammatically flawless, making it harder than ever to distinguish real emails from fake ones.
The combination of AI technology, social engineering, and gaps in human awareness has made spear phishing one of the most dangerous email threats today. This reality requires enterprises to move beyond traditional email filtering and adopt multilayer security approaches that combine technology and human training.
How Spear Phishing attacks are carried out via email
Unlike mass phishing campaigns, spear phishing follows a deliberate and carefully prepared process, where each email is tailored to a specific target. This structured approach allows many attacks to bypass both security systems and user vigilance.
A typical spear phishing email attack includes the following steps:
- Target reconnaissance: Attackers gather information from social media, corporate websites, leaked data, or previous emails to learn job roles, relationships, email habits, and project context.
- Crafting a highly credible impersonation email: Emails are written in the tone and style of a trusted sender, with realistic context and work related content that is difficult to distinguish from legitimate communication.
- Delivering the attack email: Spear phishing emails may contain malicious links, malware or ransomware attachments, fake login pages, or requests for sensitive information or urgent actions.
- Victim interaction: A single action such as clicking a link or opening an attachment can grant attackers initial access to systems or email accounts.
- Exploitation and lateral movement: Once inside, attackers steal data, commit financial fraud, or move laterally across internal systems to expand control.
Spear phishing is not random but a calculated attack chain where humans become the weakest link. Understanding each step is essential for building proactive defense strategies rather than reacting after incidents occur.
Commonly targeted individuals
Attackers do not select spear phishing targets randomly. They prioritize individuals with high exploitation value or those more susceptible to psychological manipulation.
- Employees with access to sensitive data; Such as finance, accounting, or HR staff who regularly handle confidential information and payment requests.
- New or inexperienced employees; Unfamiliar with internal processes and security culture, they are more likely to trust emails claiming to come from supervisors or internal departments.
- VAPs (Very Attacked Persons); Individuals who handle large volumes of email, interact with many partners, and have extensive public information online. Even without senior titles, they are frequent targets.
Identifying these high risk groups allows organizations to focus protection where it matters most, strengthening email defenses at the human layer.
Common spear phishing scenarios via email
Spear phishing emails come in many forms, but all exploit trust and routine work habits. Early recognition of common scenarios helps organizations reduce risk at the email intake stage.
- CEO fraud and business email compromise: Attackers impersonate senior executives and request urgent transfers or gift card purchases, often citing confidentiality or urgency.
- Malicious attachments and ransomware: Emails contain Word, Excel, PDF, or compressed files disguised as contracts, invoices, or work documents that execute malware when opened.
- Clone phishing: Attackers copy a legitimate email previously sent, replacing links or attachments with malicious content, making the email appear familiar and trustworthy.
- Trusted brand impersonation: Emails mimic banks, digital signature services, conferencing platforms, or software vendors, directing users to fake login pages to steal credentials.
Because these attacks are built around familiar contexts and user psychology, visual inspection alone is often insufficient. Enterprises must combine human awareness with advanced email security solutions.
How to identify spear phishing emails
Due to high personalization and realistic disguises, spear phishing detection should follow a structured approach rather than intuition. The SPEAR method provides a systematic way to evaluate emails before taking action.
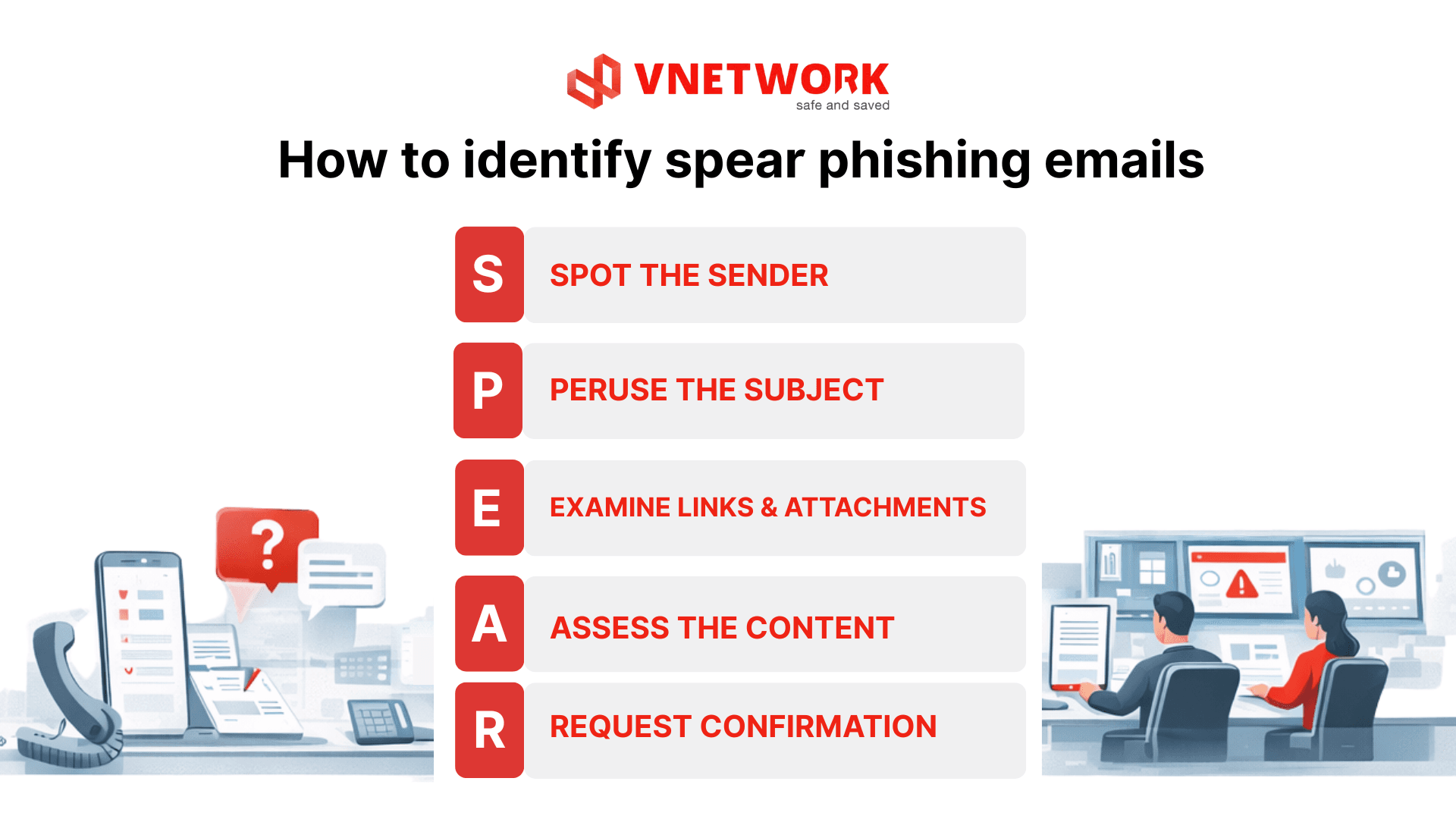
Applying the SPEAR method enables structured email verification:
- Spot the sender: Carefully inspect the actual sender address and domain for subtle discrepancies, unusual characters, or near matches to internal email addresses.
- Peruse the subject: Be cautious of subject lines that create urgency or pressure, such as “urgent” or “immediate action required.”
- Examine links and attachments: Hover over links to verify actual URLs and treat unexpected attachments with caution, especially compressed files or documents requiring macros.
- Assess the content: Evaluate whether the request aligns with your role, workflows, and current context. Unusual requests should be treated as suspicious.
- Request confirmation: When in doubt, verify through another channel such as a phone call or direct message instead of replying to the email.
When applied consistently across an organization, the SPEAR method transforms phishing detection from a reactive instinct into a proactive defense layer.
What to do if you accidentally click a spear phishing email
Accidental clicks can happen to anyone. The key is responding correctly and quickly to minimize potential damage.
- Stay calm and avoid panic
- Do not enter any additional information such as credentials or OTPs
- Disconnect from the internet immediately
- Change passwords promptly, preferably from another device
- Notify IT or information security teams with full details
- Scan the system using advanced security tools
A single mistake does not necessarily cause disaster, but delayed or improper response can. Rapid incident response combined with modern email and endpoint security is critical.
Protecting enterprises against spear phishing with VNETWORK EG Platform
Email remains the number one attack vector and the most critical defense layer. EG Platform by VNETWORK is the only email security solution in the world that fully complies with ITU T X.1236 standards issued by the International Telecommunication Union.
.jpg)
What makes EG Platform different
EG Platform is designed specifically to combat highly targeted email attacks, including spear phishing and modern APT campaigns.
- AI and machine learning driven behavioral analysis: EG Platform uses deep learning algorithms to analyze real world email behavior at the individual user level, detecting anomalies that traditional filters miss.
- Comprehensive two way email protection: The platform secures both inbound and outbound emails, preventing external attacks as well as internal data leakage and account misuse.
- Endorsed by global security organizations: EG Platform is recognized and recommended by Gartner, Rapid7, and ITSCC.
- Detection of malware free spear phishing: EG Platform identifies sophisticated phishing based on behavior, context, and risk, even when no malware or links are present, a common pattern in APT attacks.
Multi layer AI and machine learning based protection architecture
EG Platform applies a multilayer defense model, where each layer plays a specialized role:
- SpamGUARD: Filters spam, phishing, and ransomware using machine learning and SPF, DKIM, and DMARC standards.
- ReceiveGUARD: Detects 17 types of targeted email attacks in accordance with ITU T X.1236.
- SendGUARD: Prevents data leakage and 12 types of outbound email attacks.
The EG Platform AI continuously learns real user email behavior and adapts automatically to increasingly sophisticated spear phishing attacks.
Conclusion
Spear phishing is no longer a potential risk but a present and serious threat to all organizations. As attackers leverage AI to enhance their campaigns, enterprises must respond with email security solutions built on AI. EG Platform by VNETWORK delivers proactive, intelligent, and comprehensive protection against targeted email attacks.
FAQ: frequently asked questions about spear phishing
1. What is spear phishing and how is it different from phishing?
Spear phishing targets specific individuals with highly personalized emails. Unlike mass phishing, it impersonates trusted contacts or organizations, making detection difficult and potential impact severe.
2. Why does spear phishing primarily use email?
Email is the primary business communication channel and contains sensitive information. Attackers exploit daily email workflows to deliver realistic impersonation messages.
3. Can emails without malware still be dangerous?
Yes. Many spear phishing attacks rely on psychological manipulation rather than malware, tricking users into providing credentials or transferring funds. This makes traditional security tools less effective without behavioral analysis.
4. Should small businesses worry about spear phishing?
Yes. Attackers target organizations of all sizes. Smaller businesses often have weaker security controls and less training, making them attractive targets.
5. How does EG Platform prevent spear phishing?
EG Platform uses AI and machine learning to learn individual email behavior and analyze risk across the entire email lifecycle. Full compliance with ITU T X.1236 enables detection and blocking of spear phishing even without malware.
