What is spyware?
Spyware is a type of malware that infiltrates user devices without consent to monitor behavior, collect personal data, and transmit it to third parties.

Spyware silently infiltrates devices to monitor, collect, and transmit personal data to third parties.
Unlike malware that causes immediate damage, spyware operates quietly and persistently, collecting sensitive information such as:
- Login credentials and passwords
- Financial information and banking card data
- Browsing history, emails, and messages
- Enterprise data and internal information
Spyware is one of the most common cyberattack methods, leading to data breaches, financial fraud, and system performance degradation. It is particularly dangerous for enterprises.
Common types of spyware today
Spyware exists in many forms, ranging from simple advertising focused variants to highly sophisticated types capable of deep system infiltration, device control, and sensitive data theft. Understanding each spyware type helps users and organizations accurately assess risks and select appropriate defensive measures.
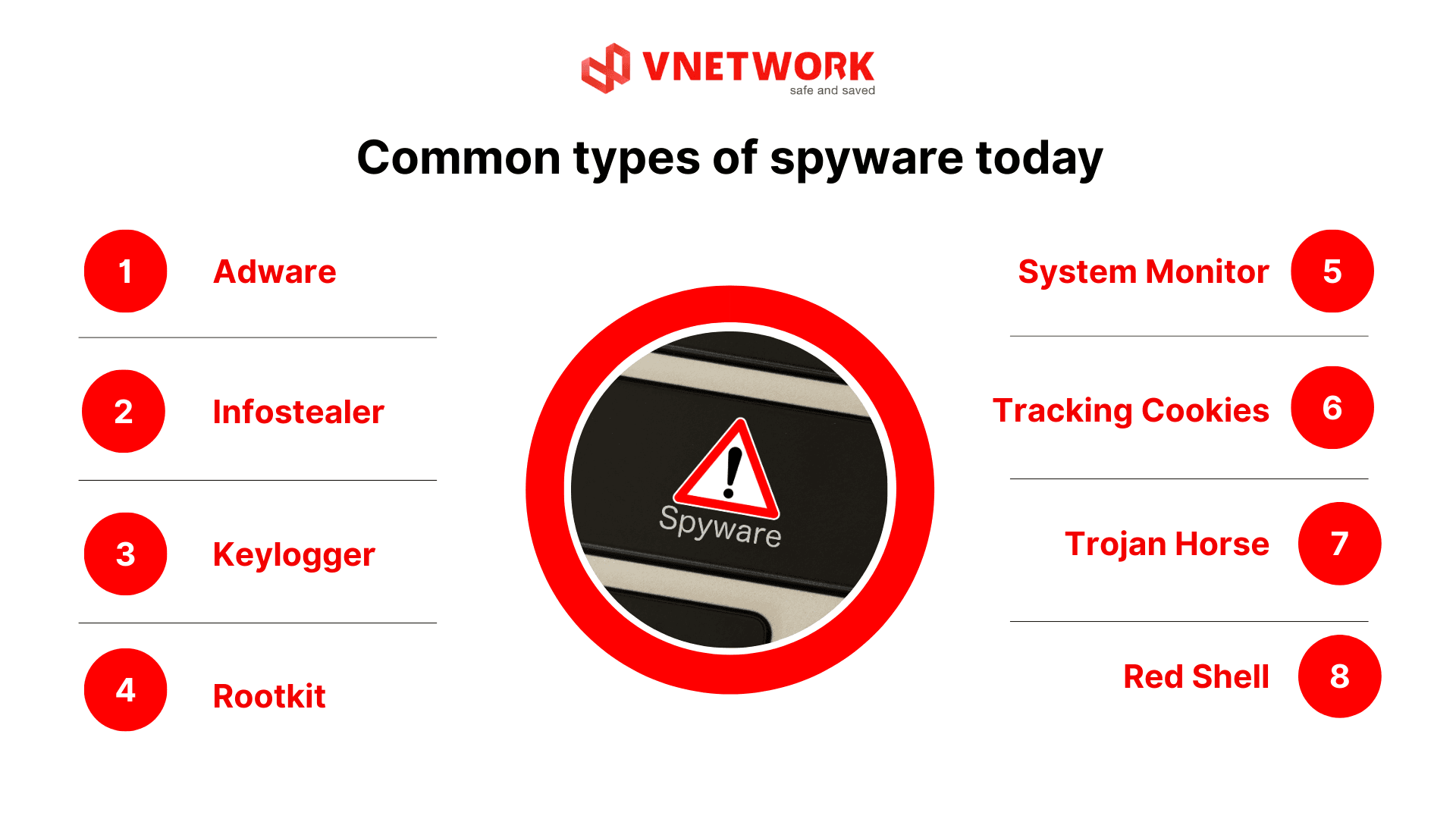
- Adware: Adware tracks user browsing behavior to display advertisements or collect data for sale to third parties. In many cases, adware also redirects users to malicious websites or spreads additional malware.
- Infostealer: Infostealers are spyware designed to steal sensitive information such as passwords, login cookies, browser data, and message content. This data is commonly used for account takeover and financial fraud.
- Keylogger: Keyloggers silently record all keystrokes, including emails, passwords, and banking information. The captured data is then transmitted to attacker servers for exploitation or resale.
- Rootkit: Rootkits embed deeply within the system and allow attackers to gain remote control over devices. Operating at low levels of the operating system, rootkits are extremely difficult to detect and nearly impossible to remove without specialized tools.
- System monitor: System monitors track all computer activities such as sent emails, visited websites, and application usage. This type of spyware is often used in long term surveillance or cyber espionage campaigns.
- Tracking cookies: Tracking cookies are installed by websites to monitor online user behavior. When abused, they can seriously violate privacy and become tools for unauthorized data collection.
- Trojan horse: Spyware is distributed through trojans disguised as legitimate software, tricking users into installing malware themselves. This is a common method to infiltrate systems without the victim’s awareness.
- Red Shell: Red Shell is a form of spyware installed during the download and installation of certain PC games. It tracks user online behavior and is typically used by developers for analytics, product improvement, and marketing campaigns, but has sparked significant privacy concerns.
Comparison of common spyware types
Each spyware type has different objectives, operating methods, and risk levels. A clear comparison helps users and organizations quickly evaluate threats, prioritize protection, and select suitable countermeasures.
| No. | Spyware type | Primary objective | Collected data | Risk level | Detection difficulty |
| 1 | Adware | Advertising revenue | Browsing behavior and history | Low to medium | Low |
| 2 | Infostealer | Information theft | Passwords, cookies, browser data, messages | High | Medium |
| 3 | Keylogger | Credential harvesting | Keystrokes, emails, passwords, financial data | High | High |
| 4 | Rootkit | System control | Full device access | Very high | Very high |
| 5 | System monitor | Long term surveillance | Emails, websites, application usage | High | High |
| 6 | Tracking cookies | Behavior tracking | Browsing habits, marketing data | Low | Low |
| 7 | Trojan horse | Spyware delivery | Depends on payload | High | Medium |
| 8 | Red Shell | User behavior analytics | Online activity and installation sources | Medium | Low to medium |
Today, spyware no longer targets only Windows computers but increasingly attacks macOS and mobile devices, especially Android and iOS smartphones. The diversity and sophistication of spyware highlight the urgent need for comprehensive and proactive security solutions to protect data and privacy in the digital environment.
How spyware works
Spyware operates silently and is difficult to detect, but behind the scenes lies a structured attack process. Understanding how spyware infiltrates, monitors, and exploits data helps users and organizations become more proactive in detection and prevention.
Most spyware follows a three stage process:
Step 1: Infiltration
Spyware is installed through:
- Phishing emails
- Fake websites
- Malicious attachments
- Freeware or cracked software
Step 2: Monitoring and data collection
After infiltration, spyware silently:
- Records keystrokes
- Captures screenshots
- Monitors browser activity
- Steals login credentials
Step 3: Data exfiltration or monetization
Stolen data is:
- Sent to attacker command servers
- Used for fraud or identity impersonation
- Sold on the dark web or to third parties
Spyware not only operates covertly after infiltration but also spreads through familiar channels that users often overlook. Effective defense requires understanding not only how spyware operates but also how it enters devices and the common disguises attackers use.
How spyware infiltrates devices
Spyware rarely infiltrates directly. Instead, it disguises itself in familiar forms and exploits user habits during internet browsing, software installation, or mobile usage. Identifying common infection vectors is critical to stopping spyware early.
Spyware commonly disguises itself through:
- Phishing attacks: Distributed via email, SMS, or fake websites that lure users into clicking malicious links or entering credentials, silently installing malware.
- Bundleware: Spyware is bundled with seemingly legitimate software, installed unintentionally when users skip advanced settings.
- Security vulnerabilities: Attackers exploit unpatched operating systems or software to install spyware without user interaction.
- Unsecured public Wi Fi: Free Wi Fi networks enable traffic interception, malware injection, or data theft.
- Malicious mobile apps: Spyware often hides in apps installed outside official stores and requests excessive permissions beyond actual functionality.
Most spyware infections originate from user behavior combined with overlooked security gaps. Once spyware infiltrates successfully, it rarely reveals itself immediately, instead operating silently over extended periods. Early detection of abnormal device behavior is therefore critical.
Signs of spyware infection
Although spyware is designed to remain hidden, it still leaves noticeable anomalies during monitoring and data collection. Early detection helps prevent severe data leakage.
- Slow performance or frequent crashes: Spyware consumes CPU, memory, and storage resources, causing sluggish performance and unexpected application failures.
- Persistent ads and pop ups: Especially with adware, intrusive advertisements appear even when not visiting ad related websites.
- Unexpected browser redirects: Automatic redirection to unfamiliar websites indicates browser or DNS manipulation.
- Unusual system setting changes: Homepage, default search engine, or system permissions change without clear user consent.
- Unknown applications or extensions: Spyware may install hidden applications or browser extensions to maintain persistence.
- Sudden spikes in network traffic: Continuous data exfiltration causes abnormal outbound traffic, a critical indicator in enterprise environments.
Note: These signs may also be associated with other malware types. Accurate diagnosis requires deep system scanning using trusted security solutions.
Recognizing these signs only identifies initial risk. To prevent ongoing data leakage and further exploitation, users and organizations must follow a structured and safe spyware removal process.
How to safely remove spyware
Delayed or improper removal can allow continued surveillance, data theft, or remote control. Spyware removal must be performed promptly and systematically.
- Disconnect from the internet to stop communication between spyware and attacker servers.
- Scan and clean the system using reputable security solutions to remove spyware, related malware, and hidden persistence mechanisms.
- Change all critical passwords after cleanup including email, banking, social media, and internal systems.
- Notify financial institutions if financial data exposure is suspected to prevent fraud.
- For enterprises, assess impact and report incidents in accordance with regulatory requirements to reduce legal and compliance risks.
Spyware removal addresses only the aftermath. Sustainable protection requires a proactive security mindset that prevents spyware from infiltrating in the first place.
How to effectively prevent spyware
Rather than reacting after an incident occurs, preventing spyware from the outset is always the most effective and lowest risk approach. Combining user awareness, security processes, and appropriate security solutions can significantly reduce the likelihood of spyware infiltration and silent data theft.
- Keep operating systems and software up to date: Security patches address vulnerabilities that spyware commonly exploits to gain initial access. Delaying updates leaves devices exposed and makes them easy targets for automated attack campaigns.
- Avoid downloading free or cracked software from untrusted sources: Many spyware strains are distributed through pirated software or so called free utilities. During installation, users may unknowingly grant malicious code deep system level permissions.
- Be cautious with emails, links, and attachments: Phishing and spear phishing emails remain the most common entry points for spyware, even when no obvious malware is attached. A single click on a malicious link can initiate surveillance and data theft.
- Install applications only from official app stores: Applications distributed outside Google Play or the Apple App Store often bypass standard security reviews and may contain embedded spyware. Restricting installation sources significantly reduces infection risk.
- Avoid using unsecured public Wi Fi networks: Open Wi Fi networks can be intercepted by attackers, allowing malware injection or data interception during transmission. Spyware may be installed without any visible indication to the user.
- Use strong passwords and multi factor authentication: Even if spyware succeeds in capturing credentials, multi factor authentication provides an additional defensive layer that limits account takeover and lateral movement.
Notably, email continues to be the number one attack vector leading to spyware and targeted attacks due to its ability to disguise malicious intent and exploit human behavior. As a result, beyond basic preventive measures, enterprises require advanced email security solutions capable of detecting modern spyware at the earliest stage of the attack chain.
This is also why traditional security solutions are increasingly insufficient, and why enterprises are turning to AI and machine learning powered email security platforms such as VNETWORK’s EG Platform.
Spyware protection: Comprehensive measures for device and system security
Spyware and related malicious threats remain persistent risks to any internet connected device. Spyware protection should therefore be understood not as a single tool or product, but as a comprehensive security strategy that combines security technologies, governance processes, and user behavior to stop spyware early in the attack chain, before data is monitored or stolen.
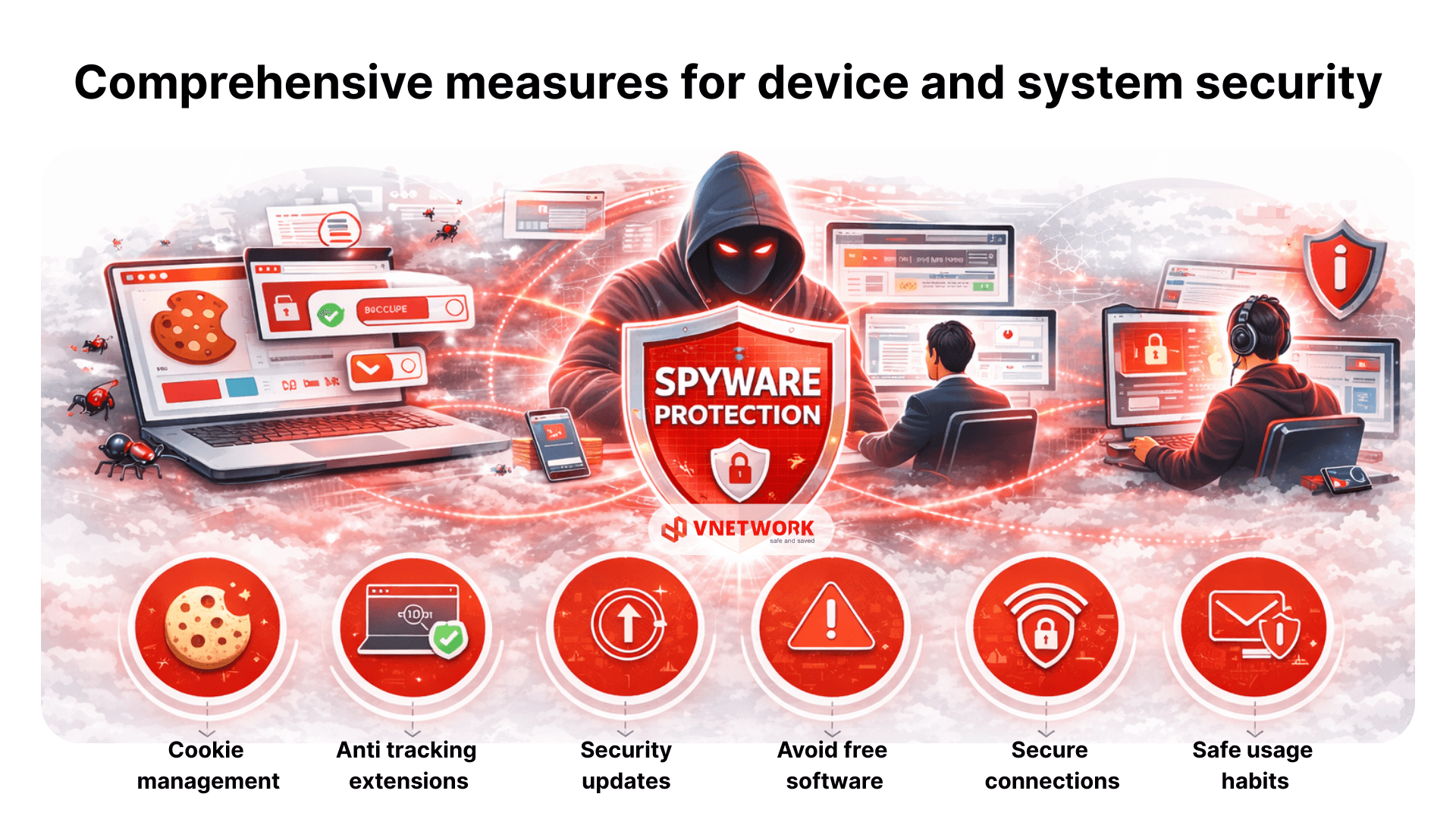
Key protection measures that significantly reduce spyware risk
- Cookie management and consent control: Users should avoid blindly clicking “accept” on all cookie consent banners. Accepting cookies only from trusted websites helps limit unauthorized tracking and data collection.
- Use browser anti tracking extensions: Installing anti tracking extensions helps block online tracking activities, not only from advertising networks but also from malicious actors, thereby enhancing privacy during web browsing.
- Keep software and operating systems updated: Regular updates are a critical component of spyware protection. Spyware frequently exploits known vulnerabilities in unpatched systems, making timely updates essential for reducing exposure.
- Avoid unverified freeware and cracked software: Free or pirated software often contains embedded spyware and data theft mechanisms. In many cases, user data becomes the hidden cost that developers monetize, posing serious information security risks.
- Use secure and trusted internet connections only: Public or unsecured Wi Fi networks are easy targets for attackers. Users should minimize the use of free Wi Fi and connect only to networks with clear and reliable security controls.
- Practice safe email and internet usage habits: User behavior plays a decisive role in spyware prevention. Avoid opening emails, downloading files, or clicking links from unknown sources, and always verify URLs and context before interacting to reduce the risk of targeted attacks.
Spyware protection for mobile devices
Spyware increasingly targets smartphones due to the large volume of personal data they contain and the continuous usage patterns of users. To protect mobile devices, the following practices are essential:
- Install applications only from official app stores: Users should download applications exclusively from Google Play Store, Apple App Store, or official publishers to reduce the risk of installing apps embedded with spyware or hidden malware.
- Carefully review application permissions: Before installation, users should carefully assess requested permissions, especially access to location, personal data, camera, and microphone, to avoid unauthorized tracking and data collection.
- Avoid clicking links in emails and SMS messages: Users should not click links directly from emails or text messages, even if the content appears legitimate. Instead, manually enter the official website URL in the browser address bar to ensure safety.
While these measures significantly reduce spyware risk, they are still insufficient in enterprise environments facing targeted spyware campaigns and sophisticated email based attacks. In practice, email remains the primary attack vector, where spyware and spear phishing are carefully disguised to bypass traditional filtering by exploiting human behavior.
For this reason, enterprises require a dedicated email security platform capable of behavioral analysis, early detection of malware free threats, and prevention of data leakage from the very beginning of the attack chain. This is precisely why VNETWORK developed EG Platform, to elevate spyware protection from basic prevention to a proactive and comprehensive enterprise email security strategy.
Protecting enterprises against spyware with VNETWORK EG Platform
As cyberattacks become increasingly sophisticated, spyware no longer appears solely as traditional malware but is often delivered through targeted emails, particularly malware free spear phishing. This allows many conventional email security solutions to be bypassed. In response, enterprises need next generation email security capable of behavioral analysis and early threat detection.
EG Platform by VNETWORK was developed specifically to meet this need and is the only email security solution in the world that fully complies with ITU T X.1236 standards issued by the International Telecommunication Union.
EG Platform is recommended by globally recognized organizations such as ITSCC, Gartner, and Rapid7.
EG Platform leverages artificial intelligence and machine learning and is designed with an AI first architecture to enable:
- Two way email protection for inbound and outbound traffic: Unlike solutions that focus solely on inbound emails, EG Platform implements two way protection for both incoming and outgoing emails. This enables enterprises to block spyware and phishing from external sources while also preventing data leakage and misuse of compromised internal accounts to launch outbound attacks.
- Detection of malware free spyware and spear phishing: Modern spyware often contains no malicious attachments and instead exploits human psychology and behavior. EG Platform applies behavioral analysis and targeted attack detection, and as the only solution fully compliant with ITU T X.1236 standards, it can detect spear phishing emails even when they contain no links or malware, allowing enterprises to stay ahead of attackers.
- Learning real world email behavior for each individual user: EG Platform’s AI continuously learns and builds a unique email behavior baseline for every user within the organization. As a result, emails exhibiting anomalies such as changes in writing style, sending time, or interaction patterns can be detected early, even if they bypass traditional security layers.
- Early prevention of data leakage and APT attacks: By combining behavioral analysis, two way protection, and outbound content control, EG Platform prevents data leakage, email account takeover, and advanced persistent threats at the earliest stage, before serious damage occurs.
In the face of increasingly sophisticated spyware and email based attacks, enterprises can no longer rely solely on traditional security solutions. With full compliance to ITU T X.1236 standards, advanced AI and machine learning capabilities, and endorsements from Gartner, Rapid7, and ITSCC, EG Platform by VNETWORK delivers a proactive, modern, and comprehensive approach to protecting enterprise email, data, and reputation in today’s high risk digital environment.
FAQ - Frequently asked questions about spyware
1. What is spyware?
Spyware is malicious software that secretly infiltrates devices to monitor, collect, and transmit personal data to third parties without user consent.
2. What type of software is spyware?
Spyware is a form of malware designed for surveillance, behavior tracking, and theft of sensitive information such as passwords, financial data, and enterprise data.
3. Does spyware require an internet connection to operate?
Spyware can collect data while offline, but it requires internet access to transmit collected data to attackers or third parties.
4. How can spyware be detected early?
Users should monitor abnormal signs such as slow system performance, browser redirection, and unexpected advertisements, and use advanced security solutions to perform deep system scans.
5. What should enterprises do to prevent spyware effectively?
Enterprises should combine security awareness training, multi layer email security, and AI driven solutions such as EG Platform to detect targeted attacks at an early stage.
