1. What Is Ransom DDoS?
Ransom DDoS, also known as RDDoS, refers to distributed denial-of-service attacks combined with extortion demands. It is a particularly dangerous form of cyber attack where threat actors leverage botnets or exploit vulnerabilities to overwhelm or paralyze a victim's service infrastructure while simultaneously sending threats to escalate the disruption or maintain the outage unless a ransom is paid.

Unlike traditional DDoS attacks that solely aim to disrupt operations, RDDoS incorporates a financial motive, compelling victims to pay to halt or prevent intensified assaults.
2. Why are businesses becoming prime targets?
Ransom DDoS attacks are escalating rapidly not only due to their severity but also because businesses increasingly represent ideal targets. Several factors are empowering attackers more than ever, from low execution costs and reliance on digital infrastructure to the proliferation of attack-for-hire services on the dark web.
- Low costs with high impact: According to VNETWORK reports, over 360,000 DDoS attacks were recorded in 2024, marking a 20% increase from the previous year. Notably, Ransom DDoS (RDDoS) incidents rose sharply by 28%, indicating the growing prevalence of this attack method.
- Heavy dependence on digital infrastructure: Digital transformation and online service operations make businesses vulnerable to immediate paralysis during outages, enabling attackers to exert pressure for ransom payments.
- Explosion of DDoS-for-Hire trends: For as little as 10 to 20 USD, cybercriminals can rent botnets or DDoS services, making it effortless and inexpensive to launch widespread attacks.
- Damages beyond finances: Attacks result in not just recovery downtime but also brand reputation harm, customer loss, and potential sensitive data leaks if accompanied by system intrusions.
3. Signs to identify if your business is under Ransom DDoS Attack
Ransom DDoS attacks often strike abruptly, making early detection challenging without robust monitoring systems. However, certain warning signs can help you spot and respond promptly before damages escalate.
- Online services slow down or halt: Websites, applications, or service portals experience unusual loading delays, interruptions, or complete inaccessibility, especially during peak hours.
- Abnormal traffic spikes: Systems log sudden surges in requests from diverse IP addresses or repeated high-frequency queries from a single IP, detectable through server logs.
- Receipt of warnings or extortion messages: Businesses receive emails, messages, or notifications with threats such as "We have attacked you; pay up or we will continue or escalate the assault."
- Monitoring systems alert overload: Security dashboards or monitoring tools signal massive traffic volumes, bandwidth thresholds being hit, leading to server overload or unresponsiveness.
4. How attackers execute RDDoS
Ransom DDoS perpetrators follow a deliberate sequence of steps, from tool preparation to psychological pressure, to coerce victims into paying. Understanding these phases enables early detection and precise preventive measures before damages spread.
- Botnet preparation: Utilizing infected devices, unsecured IoT networks, or remotely controlled servers.
- Demonstration phase: Attackers launch a small-scale assault to prove their capabilities and build psychological pressure on the victim.
- Main phase: After assessing responses, attackers deploy large-scale strikes at network layers (Layer 3/4) or application layers (Layer 7) to disrupt services.
- Attachment of ransom demands: Alongside the attack, messages demand payment in exchange for ceasing or not escalating the intensity.
- Psychological control: By demonstrating pressure and potential losses, they induce fear of greater harm, prompting businesses to consider ransom payments.
5. Severe consequences of RDDoS
Ransom DDoS (RDDoS) attacks extend beyond temporary disruptions, inflicting profound impacts on finances, reputation, and information security. When systems crash or slow abnormally, damages ripple across revenue, trust, operational costs, and security risks.
Here are the serious repercussions businesses may face without timely responses:
- Immediate revenue loss: Online service interruptions block transactions, orders, and customer interactions, severely affecting e-commerce platforms, fintech, online gaming, and real-time dependent services.
- Reputation decline and customer churn: Clients depart, partners lose confidence, and brand damage persists long-term; restoring trust often demands more time and expense than technical fixes.
- Escalating remediation costs: Businesses incur extras for backup bandwidth, server scaling, scrubbing services, incident investigations, and regulatory reporting, amplifying both direct and indirect expenses.
- Cascading risks: Many DDoS incidents serve as diversions for deeper intrusions, leading to data breaches, encryption, or concurrent ransomware, heightening overall security threats.
Faced with heavy losses, some businesses may be tempted to pay for peace. However, this is not a secure approach, as payments offer no guarantee of cessation and instead encourage criminals, positioning the business as a repeat target.
The right strategy involves system recovery, fortified defenses, and close collaboration with cybersecurity experts to prevent recurrences!
6. Current statistics in Vietnam and Globally
VNETWORK reports documented over 360,000 DDoS attacks in 2024, a 20% rise from the prior year. Among them, ransom DDoS incidents, involving extortion elements, surged by 28%, highlighting the increasing commonality of this threat.
Entering the first half of 2025, VNETWORK tallied approximately 256,000 DDoS attacks in just six months, a sharp increase over the previous year's equivalent period, reflecting accelerating attack intensity.
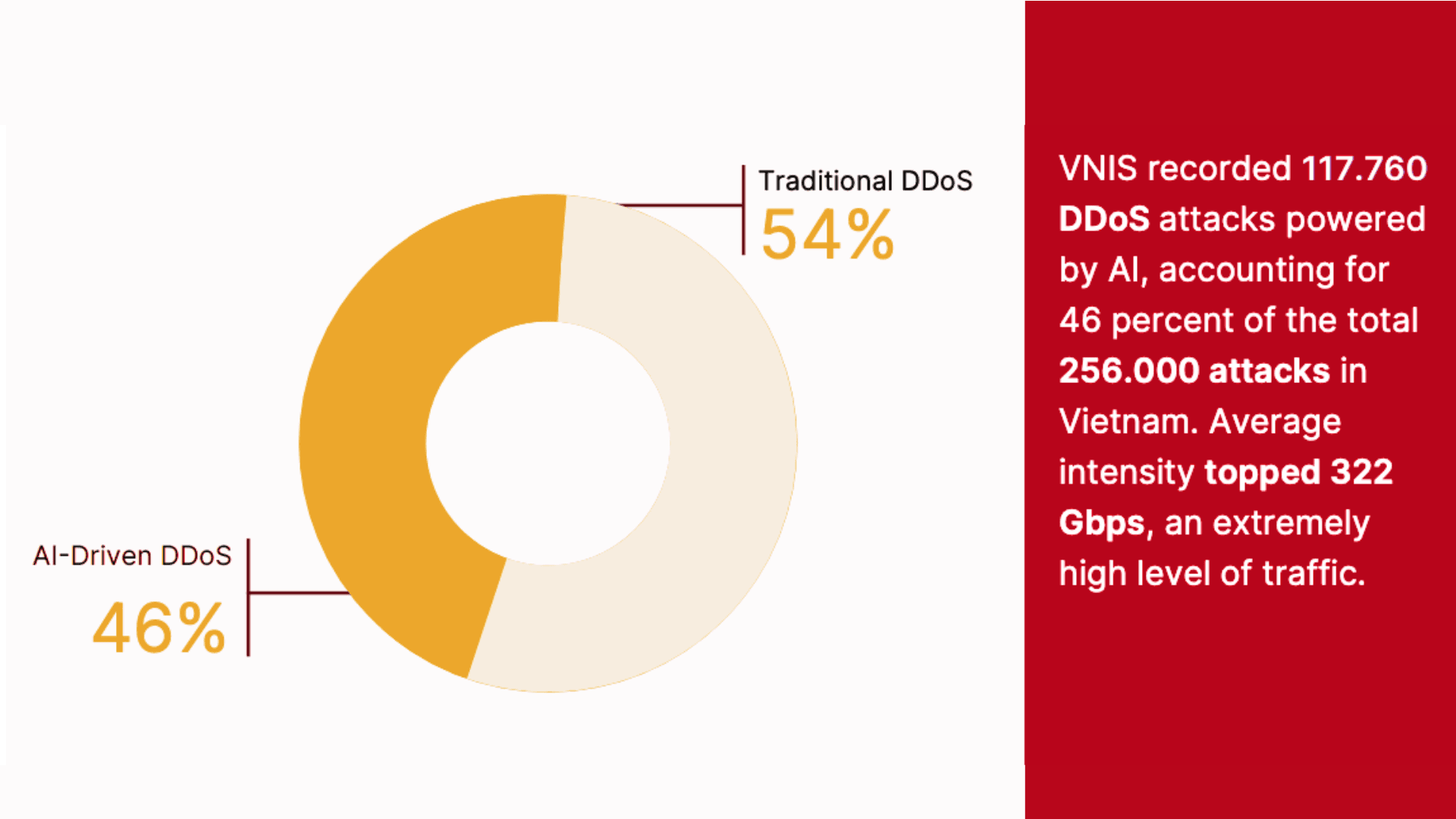
Global reports also indicate a 68% rise in ransom DDoS during Q2 2025, underscoring the widespread escalation of this menace. In Vietnam, finance and securities sectors are most targeted, accounting for 26% of total DDoS attacks, per VNETWORK's VNIS system statistics.
7. Effective prevention and Response solutions: Guidance from VNETWORK
VNETWORK's VNIS Platform offers a comprehensive security suite for Web/App/API, delivering enterprise-grade measures to counter RDDoS.
7.1 Technology and defense techniques
- Invest in specialized multi-layer DDoS mitigation: Covering Layer 3/4 and Layer 7 to guard against volumetric floods and HTTP(S) floods.
- Separate dynamic-static loads and enable degraded mode: To alleviate backend strain and maintain basic user experience during assaults.
- Adopt multi-cloud/multi-region strategies: Avoiding single points of failure, ensuring continuity in unaffected regions during targeted attacks.
7.2 Monitoring and early detection
- Establish real-time traffic monitoring (SOC/IDS): To identify anomalies at the onset of attacks.
- Conduct regular DDoS testing and drills: Preparing businesses for swift RDDoS responses.
- Leverage VNIS Platform with over 2,400 WAF rules, infrastructure exceeding 2,600 Tbps, and CDN PoPs spanning 146 countries, ensuring load-bearing capacity and traffic distribution.
7.3 Response and operational procedures
- Develop incident response plans: Aiming for rapid recovery (RTO ≤10 minutes) with periodic drills.
- Prepare RDDoS-specific scripts: Upon threats, follow protocols: avoid ransom payments, report to authorities, and collaborate with experts.
- Partner with reputable cybersecurity providers like VNETWORK for 24/7 support during large-scale incidents.
7.4 Management and financial aspects
- Budget for DDoS costs (FinOps): Including egress, scrubbing, WAF requests, and automated load-shedding thresholds for financial control.
- Integrate DDoS prevention into strategic risk management: Ensuring leadership views it as a business risk, not merely a technical issue.
8. Why choose VNIS platform from VNETWORK?
Amid evolving DDoS and Ransom DDoS (RDDoS) threats, businesses require robust, reliable, and easy-to-deploy security solutions. VNETWORK's VNIS Platform meets these needs fully, blending global infrastructure, advanced security technologies, and experienced experts to ensure uninterrupted and secure operations.
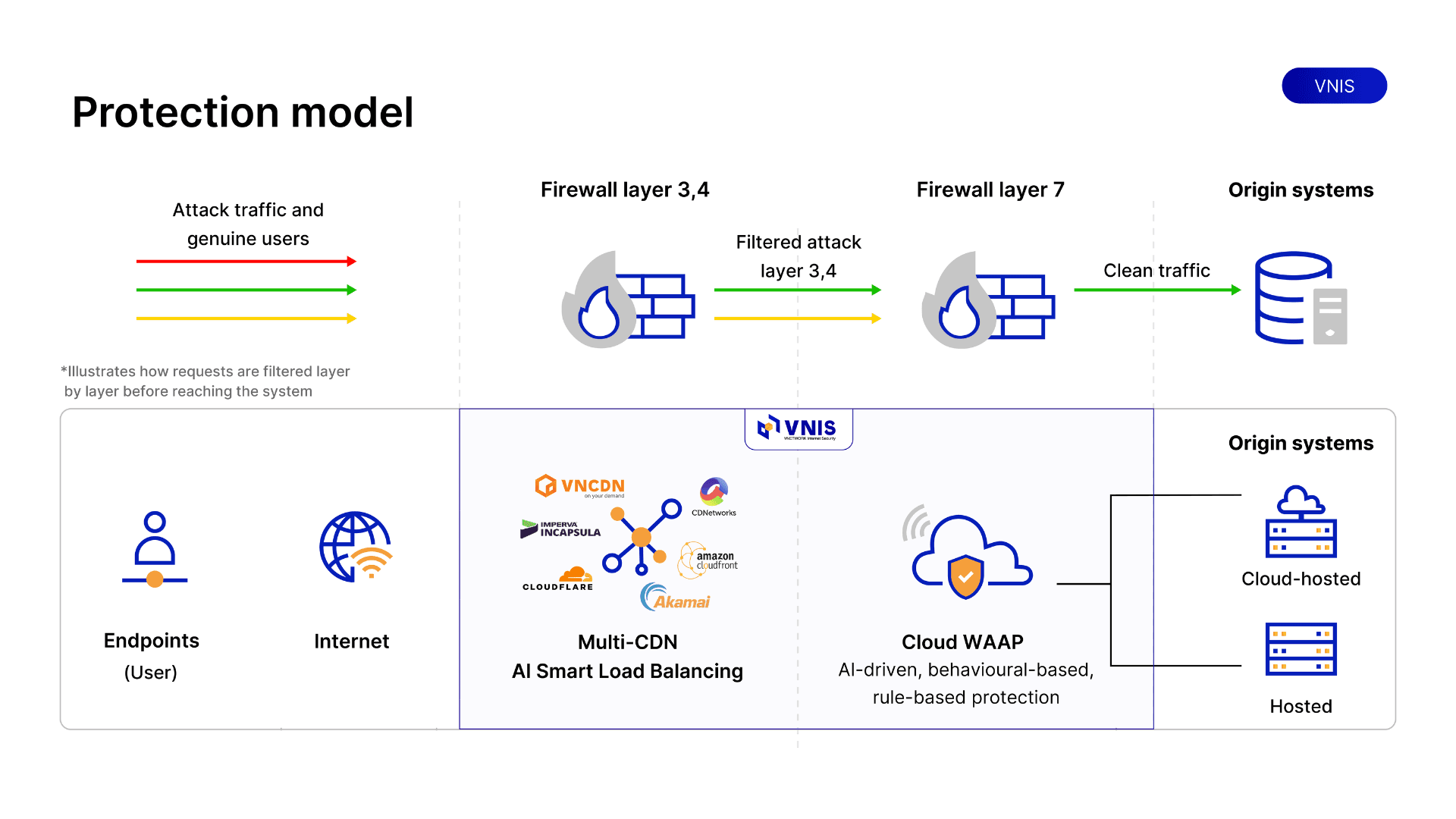
- Superior infrastructure: Featuring over 2,300 CDN PoPs worldwide, up to 2,600 Tbps capacity, and coverage in more than 146 countries, guaranteeing fast and stable delivery for any business.
- Leading security technologies: Equipped with over 2,400 OWASP-compliant WAF rules, continuously updated to block emerging vulnerabilities and attack vectors.
- User-friendly management interface: Intuitive platform for overseeing multiple security layers in one view, saving time and resources.
- Global expert team: Backed by 24/7 SOC operations, involving domestic and international cybersecurity specialists for rapid threat responses.
- Service level agreement (SLA) commitments: VNETWORK guarantees consistent performance and security, enabling seamless business continuity.
With VNIS, businesses gain protection not only from standard DDoS but also effective countermeasures against increasingly sophisticated RDDoS extortion tactics.
9. Conclusion
RDDoS is no longer a potential threat but a stark reality with surging frequency and scale. Statistics from Vietnam to global trends confirm that businesses must proactively fortify defenses.
Rather than reacting passively to attacks, invest in comprehensive security like VNETWORK's VNIS to ensure ongoing protection, service continuity, reputation strengthening, and focus on business growth. Do not let your enterprise become easy prey for cybercriminals. Act today!
FAQ - Common questions about Ransom DDoS
1. How does Ransom DDoS differ from standard DDoS?
Ransom DDoS (RDDoS) not only disrupts services but also includes demands for ransom payments to stop or avoid escalation. Standard DDoS focuses solely on paralysis without financial extortion.
2. What should businesses do immediately upon receiving a DDoS threat letter?
Avoid paying the ransom independently. Document the threat, alert your security team, activate load-reduction modes, and contact experts like VNETWORK to initiate defenses.
3. Do small businesses need to worry about RDDoS like large corporations?
Yes, any business reliant on online services is a potential target. Botnet rentals and attack costs are low and accessible, making the risk real for all.
4. What infrastructure is needed for effective RDDoS prevention?
A multi-layer strategy: Layer 3/4 and Layer 7 DDoS protection, DNS/API security, load separation, multi-region setups, 24/7 monitoring, and clear response procedures, as implemented in VNETWORK's VNIS solution.
5. Should you pay the ransom if hit by RDDoS?
No, as payments provide no assurance of attack cessation and incentivize criminals. Prioritize technical recovery and expert consultation for defenses.
