What is DDoS?
DDoS (Distributed Denial of Service) is a denial-of-service attack in which attackers leverage multiple compromised devices, such as computers, servers, and IoT devices within a botnet—to flood the target system with a massive volume of illegitimate traffic simultaneously. The goal is to exhaust server resources, rendering websites or applications unable to respond to legitimate user requests.
Unlike traditional DoS attacks, which originate from a single source, DDoS operates in a distributed manner, sourcing traffic from numerous IP addresses across diverse geographic locations. This makes detection and mitigation significantly more challenging, especially for servers lacking advanced security measures. In simple terms, when the system is forced to process far more requests than it can handle, the server becomes overloaded, slows down dramatically, or shuts down completely.
Why are DDoS attacks so dangerous?
DDoS ranks among the most threatening denial-of-service attack types today, due to its scale, ease of execution, and the severe business impact it delivers.
Low cost and ease of execution
In the past, launching a DDoS attack required advanced technical expertise and substantial infrastructure. Today, the rise of DDoS-for-hire services has made these attacks accessible to almost anyone.
According to the VNETWORK DDoS attack report for the first half of 2025, systems in Vietnam recorded over 256,000 DDoS incidents—an increase of 87,000 cases (+51%) compared to the same period in 2024, averaging 42,700 attacks per month. For a modest fee, attackers can rent botnets capable of generating overwhelming traffic volumes sufficient to take down servers belonging to many small and medium-sized enterprises.
Significant financial losses
The most immediate consequence of a DDoS attack is service downtime. When websites or applications become unavailable, businesses suffer direct revenue loss, alongside substantial costs for incident response and system recovery. Beyond that, repeated disruptions erode brand reputation and customer trust, particularly in sectors such as e-commerce, finance, and online services.
Difficult to detect and mitigate promptly
Modern DDoS attacks often involve massive botnets with spoofed IPs and multiple simultaneous vectors. With AI assistance, attacks can dynamically adapt, mimic legitimate user behavior, and automatically shift traffic patterns. VNETWORK data shows that 46% of DDoS incidents in Vietnam (more than 117,000 attacks) involved AI during the first half of 2025. This evolution makes malicious traffic increasingly hard to distinguish from legitimate requests.
A stepping stone for larger attacks
In many cases, DDoS serves not as the primary objective but as a distraction. While security teams focus on handling the flood of traffic, attackers may exploit vulnerabilities to gain unauthorized access, steal data, or deploy ransomware. This dual-threat nature elevates DDoS from a mere service disruption to a comprehensive risk to organizational information security.
How do DDoS attacks work?
To appreciate why DDoS can cripple systems so quickly, it helps to understand the typical attack workflow:
- Botnet construction: Attackers infect a large number of internet-connected devices (computers, servers, IoT) with malware, turning them into remotely controlled "bad bots."
- Centralized command: Through a command-and-control infrastructure, the attacker directs the entire botnet to target a specific IP address or system.
- Massive traffic generation: Each bot sends continuous connection requests or data packets, creating an abnormal surge in traffic from diverse global sources.
- Resource exhaustion: The target server expends bandwidth, CPU, and connection buffers processing invalid requests, leaving no capacity for legitimate traffic.
- Service denial: Overloaded resources cause websites or applications to slow, error out, or become entirely inaccessible, directly impacting user experience and business continuity.
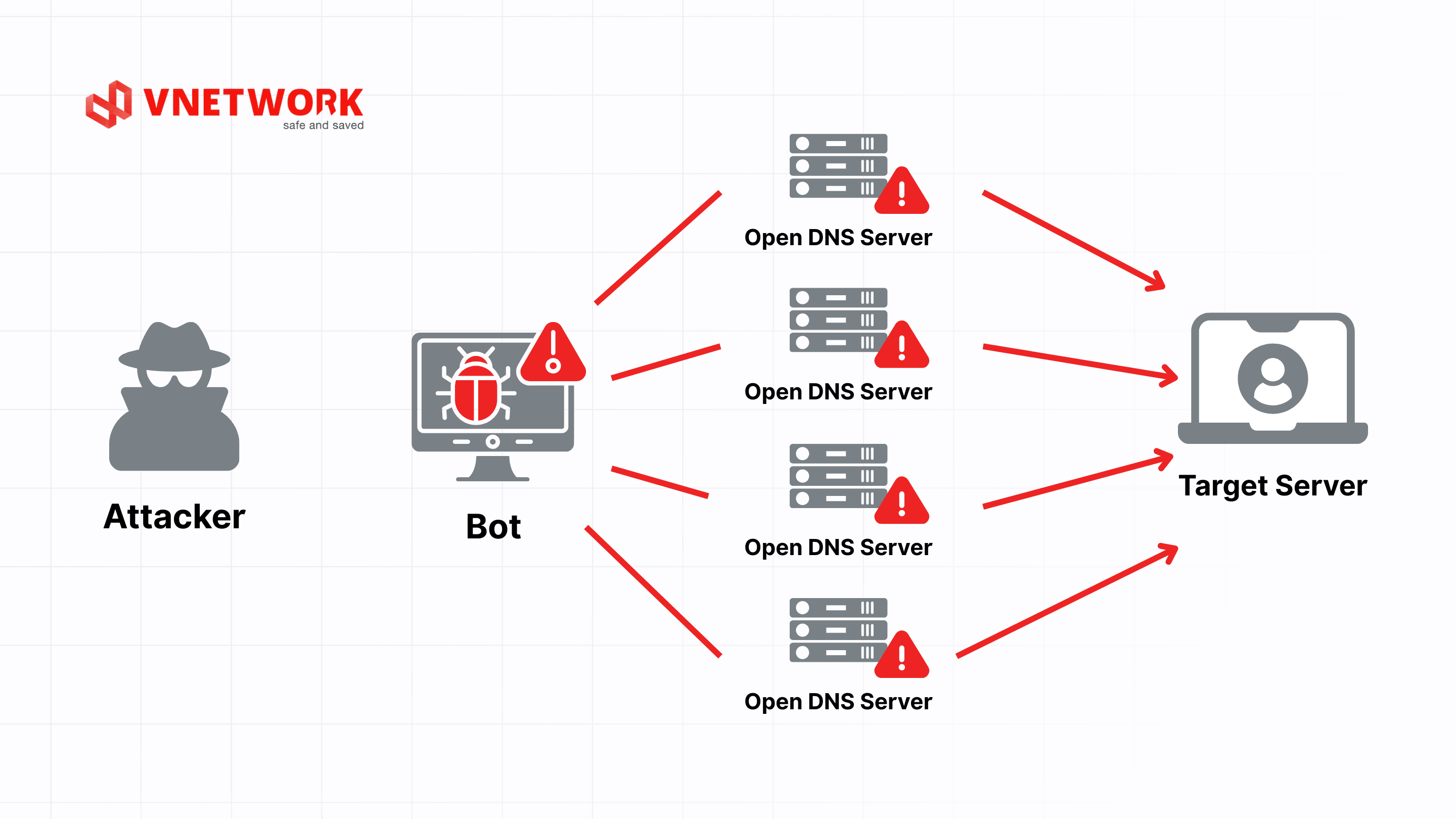
How to recognize a DDoS attack
Early detection relies on monitoring unusual changes in traffic patterns, response times, and system behavior. Key indicators include:
- Website slowdown or inaccessibility, even when underlying infrastructure appears healthy.
- Sudden spikes in traffic originating from numerous unfamiliar IP addresses.
- Repetitive requests following consistent patterns or targeting sensitive endpoints.
- Frequent server errors, timeouts, or abrupt connection resets.
- Complete saturation of bandwidth, CPU, or connection queues, preventing service to legitimate users.
Common types of DDoS attacks
Volumetric attacks
These target lower layers of the OSI model (primarily Layer 3/4), aiming to saturate network bandwidth rather than exploit applications.
- UDP Flood: Floods the network layer with invalid UDP packets, rapidly consuming bandwidth and processing resources.
- ICMP Flood (Ping Flood): Overwhelms servers with ICMP echo requests, exhausting network-layer resources through constant replies.
- NTP/DNS Amplification: Exploits third-party servers to amplify traffic, delivering massive payloads to the target with minimal attacker effort.
Protocol attacks
These deplete internal server resources by exploiting protocol handling, often without generating extreme bandwidth volumes.
- SYN Flood: Forces servers to maintain incomplete connection states, exhausting memory and connection tables.
- Ping of Death: Sends malformed packets that cause errors during processing, potentially crashing vulnerable systems.
- IP Null/Fragment Flood: Uses incomplete or fragmented packets that require excessive reassembly effort, degrading overall performance.
Application-layer attacks (Layer 7)
These directly target the application layer or layer 7, where websites, APIs, and digital services operate. The danger lies in requests that closely mimic legitimate user behavior, making them difficult to filter.
- HTTP Flood: Overwhelms servers with seemingly valid HTTP requests, gradually consuming processing resources.
- Slowloris: Maintains long-open connections to tie up server resources without high traffic volume.
- Misused Application Attack: Abuses legitimate features like search, login, forms, or API calls beyond intended limits.
Zero-day DDoS
These exploit previously unknown vulnerabilities without available patches, affecting any layer from network infrastructure to applications. Such Zero-day attacks leave organizations with little immediate defense, often resulting in prolonged downtime and significant financial damage.
Experimental DDoS attack guide
Cybercriminals launching DDoS attacks on websites or applications not only cause business losses but also severely degrade customer experience. During an active attack, users cannot access services or complete transactions.
Numerous free tools are available to simulate DDoS attacks for educational purposes, helping teams understand the real danger of distributed denial-of-service. One commonly referenced tool is LOIC (Low Orbit Ion Cannon), originally developed by Praetox Technology and notably used by the Anonymous hacker group.
Steps to simulate a DDoS attack using LOIC:
Step 1 - Download LOIC
Obtain the tool from SourceForge. Disable antivirus warnings (for testing only) and extract the ZIP file.
Step 2 - Launch LOIC and configure the attack
Open the application to access configuration options, including target IP/URL, port, thread count, and attack speed.
Step 3 - Confirm and initiate
After setup, select the activation button to start the simulation and observe the attack in progress.

After testing the attack simulation, the attacked website will consume a large number of resources because it has to process all requests from the large amount of invalid traffic generated by the DDoS.
To overcome the situation of attacks that disrupt access as well as minimize the damage caused by cybercriminals to businesses, let’s work with VNETWORK to learn and choose effective anti - DDoS tools.
How to prevent DDoS attacks
Here are some common DDoS attack prevention methods that businesses and organizations often apply to protect their systems against increasingly sophisticated attacks.
Scale bandwidth and leverage CDN
One fundamental yet powerful defense is increasing system capacity. Sufficient bandwidth makes it harder for attacks to saturate the entire service. Integrating a Content Delivery Network (CDN) distributes traffic across multiple global points, preventing overload at any single server and maintaining stable access for legitimate users even during attacks.
Web Application Firewall (WAF)
A WAF acts as a protective layer in front of websites and applications, inspecting incoming requests, detecting anomalies, and blocking malicious behavior before it reaches the origin server. It is particularly effective against application-layer DDoS, reducing server load by filtering unnecessary or abusive requests.
Rate limiting
Rate limiting restricts the number of requests an individual user or IP can submit within a given timeframe. This effectively curbs bursty abusive patterns, allowing servers to prioritize genuine traffic and reduce exploitation of features like login, search, or API endpoints.
Continuous monitoring and early detection
Real-time system monitoring is essential for DDoS defense. Tracking traffic and performance metrics enables early identification of anomalies, allowing technical teams to respond proactively before attacks cause major disruption and minimizing revenue and user experience impact.
VNIS - Comprehensive DDoS protection solution
VNIS, VNETWORK's Web/App/API security and acceleration platform, empowers organizations to proactively counter cyber threats. It delivers real-time protection against multi-layer DDoS (Layers 3/4/7), malicious bots, vulnerability exploits such as SQL Injection and XSS, zero-day threats, malware, and dangerous crawlers. Powered by AI, VNIS detects and blocks abnormal behavior early while preserving performance and user experience.
Beyond security, VNIS ensures speed and stability for websites and applications under high traffic conditions. Operating on a global infrastructure with over 2,300 Points of Presence (PoPs) in more than 146 countries, it handles up to 2,600 Tbps of traffic and more than 10 billion daily requests. With over 2,400 active security rules, VNIS currently safeguards more than 400,000 websites, applications, and APIs against large-scale DDoS attacks.
VNIS operating model
VNETWORK's VNIS follows a dual-layer protection architecture, delivering robust DDoS defense across both network and application layers.
- Layer 1: Combines AI Smart Load Balancing and Multi-CDN to counter infrastructure-layer DDoS. AI analyzes access behavior, intelligently distributes traffic, and eliminates abnormal sources before they overwhelm the system.
- Layer 2: Deploys WAAP (Web Application and API Protection) powered by AI to block application-layer DDoS, malicious bots, and common vulnerabilities listed in OWASP Top 10. This layer safeguards the core logic of web, app, and API services where deep exploitation often occurs.
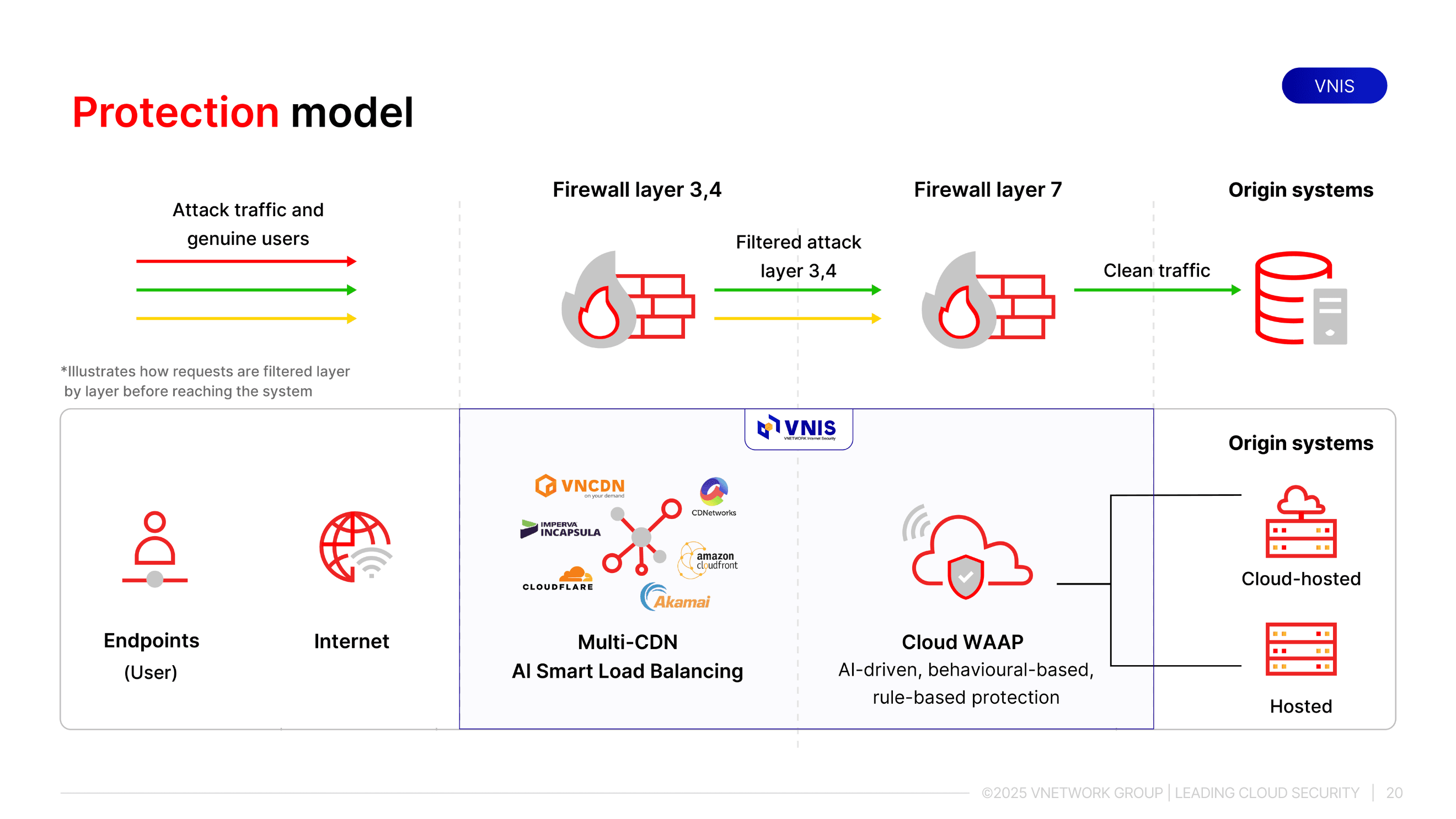
Through tight integration of these layers, VNIS not only stops DDoS attacks effectively but also enables secure, stable, and scalable operations in a volatile digital landscape. Contact VNETWORK today for tailored VNIS consultation and safeguard your website and applications against all DDoS risks!
FAQ – Frequently asked questions about DDoS attacks
1. What is a DDoS attack?
A Distributed Denial of Service (DDoS) attack overwhelms a system with massive illegitimate traffic, preventing it from serving legitimate users.
2. Who do DDoS attacks typically target?
Any internet-connected system can be targeted, especially enterprise websites, e-commerce platforms, financial applications, online gaming, and APIs.
3. Does DDoS cause data loss?
DDoS primarily disrupts service availability, but attackers often use it as cover to execute deeper breaches, such as data exfiltration or malware deployment.
4. Is launching a DDoS attack easy?
Yes, thanks to DDoS-for-hire services and accessible botnets, even non-expert attackers can cause substantial damage today.
5. Are CDN and WAF sufficient to stop DDoS?
They significantly reduce risk, but large-scale, multi-vector, or sophisticated application-layer attacks require specialized, comprehensive solutions.
6. How does VNIS differ from standard DDoS protection?
VNIS integrates Multi-CDN, AI Smart Load Balancing, and WAAP for end-to-end defense from network infrastructure to application logic, while maintaining high performance.
7. Does VNIS slow down websites or applications?
No, VNIS is engineered for both security and acceleration, ensuring stability and speed even under elevated traffic or during active attacks.
8. Do small businesses need DDoS protection?
Yes, smaller organizations are frequent targets due to limited defenses, and even brief DDoS incidents can cause serious operational disruption.