In the first quarter of 2021, the DDoS attack situation had several “hot spots”. Remote working and learning continue to create opportunities for hackers to attack. It’s not just legitimate organizations that are targeted by hackers. Now, underground networks are also not immune to the fate of being attacked. The report below will share more details about the DDoS attack situation in the last quarter of 2021.
Overview of DDoS attack situation
The first quarter of 2021 saw the emergence of two new botnets. The first was news about FreakOut malware attacking Linux devices that hit the headlines earlier this year. Hackers have exploited some serious vulnerabilities in the program installed on the victim’s machine. Including the recently discovered CVE-2021-3007. The botnet cybercriminals use malware-infected devices to perform DDoS attacks or mine cryptocurrency.
FreakOut Malware Attacks Linux Devices
The other botnet is an active bot focused on Android devices with the ADB (Android Debug Bridge) debug interface. This botnet is called Matryosh (derived from the Russian word matryoshka - a type of doll). Because they have to go through many steps to get the C&C address. This is not the first bot to attack mobile devices via the debug interface. Previously, ADB.Miner, Ares, IPStorm, Trinity, and other malware have also exploited this vulnerability.
Q1 also saw the return of Mirai. Hackers have infected network devices, exploiting new vulnerabilities or unknown bugs. According to experts, this attack has affected thousands of devices.
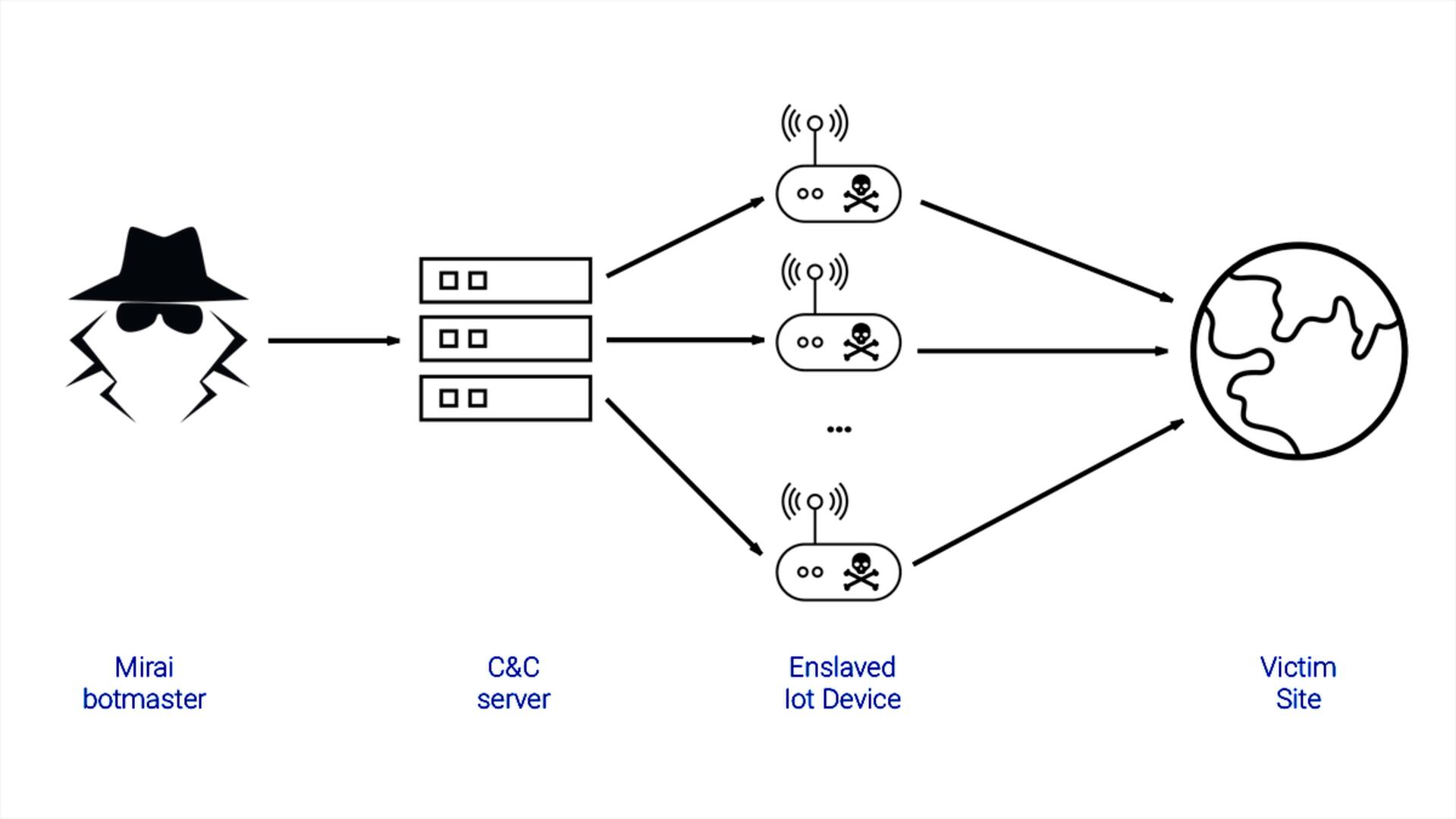
The Mirai botnet is back too
In Q1, cybercriminals used many new tools to amplify DDoS attacks. One of them is Plex Media Server to set up a media server on Windows, macOS, or Linux operating system, network-attached storage (NAS), digital media player…About 37,000 Plex installed devices Media Server is very vulnerable to attack. Although they can access the network directly or receive packets from a specific UDP port. Plex Media Server generates junk traffic from Plex Media Service Discovery Protocol (PMSSDP) requests and amplifies the attack to about 4.68.
Amplifier Vector is primarily an RDP service for remote connection to Windows devices. The RDP server listening on UDP port 3389 is used to amplify DDoS attacks. 33,000 vulnerable devices were found at the time of publication of the misuse of remote access services. The gain is much higher than in the case of Plex Media Server: 85.9. To prevent attacks over RDP, you should hide the RDP server behind the VPN or disable UDP port 3389.
That is not to say that a VPN is a secure solution as it is also vulnerable to amplification attacks. During Q1 2021, hackers hunted down Powerhouse’s VPN servers. The culprit turned out to be the Chameleon protocol. This is a protocol that protects against VPN blocking and listens on UDP port 20811. The server response on the Chameleon port is 40 times larger than the original request. So the vendor had to release a patch for this issue.

VPNs are also vulnerable to amplification attacks
However, not all users update the patch in time. As of mid-March, there are about 4,300 web servers used to amplify DDoS over the DTLS protocol. These devices are misconfigured or not updated to the latest version. Cybercriminals wasted no time using this amplification method to carry out DDoS attacks.
Hackers see not only the non-standard protocol as a means of amplification but also as a tool for carrying out DDoS attacks. In Q1, a new attack vector appeared in the form of DCCP (Datagram Congestion Control Protocol). It is a transport protocol to adjust the network load when transmitting data in real-time. Anti-congestion mechanisms do not prevent this attack protocol. As a result, many requests are generated, flooding many users. Furthermore, on the part of the receiver of the spam packet, no DCCP application can access it online. Most likely because attackers are trying to bypass DDoS Protection standards.
Another unusual DDoS vector has been alerted by the FBI. They have warned of an increase in attacks on emergency dispatch centers. TDoS (telephone denial of service) attacks aim to keep the victim’s phone number busy and flooded with spam calls. There are 2 main methods of TDoS: through flash mobs on social networks or forums and automated attacks using VoIP software. While TDoS attacks are not new, they prevent people from accessing emergency services.

TDoS attacks prevent people from accessing emergency agencies
Overall, this quarter was full of distributed denial-of-service attacks that were reported by the media. In particular, DDoS ransomware continued to attack organizations around the world earlier this year. In some cases, the ability of hackers to attack DDoS is surprisingly large. For example, a European casino company was hit by spam traffic, peaking at 800GB/s. Maltese Internet service provider Melita was also hit by a ransomware attack. That DDoS attack disrupted the ISP’s services. At the same time, ransomware attackers stole data before encryption. They view DDoS attacks as a tool of extortion. The first attack occurred late last year when the victim refused to negotiate. In January, cybercriminals using Avaddon also jumped into the fray. In March, the Sodinokibi (REvil) ransomware attack group also joined.
Increased Ransomware could be attributed to the cryptocurrency price continuing to rise in Q1 2021. In early February, Tesla announced a large investment in Bitcoin, boosting the cryptocurrency. As a result, some crypto exchanges cannot cope with a large number of subscribers, leading to downtime. British exchange EXMO was also hit by a DDoS attack. The company acknowledged that the attack affected the entire network infrastructure, not just the website.
As many users are still working and operating from home in Q1 2021. As a result, attackers are targeting the resources most used by users. In addition to the aforementioned Melita, Austrian supplier A1 Telekom and Belgian telecommunications company Scarlet were also hit by DDoS attacks (though no ransomware). In both cases, their customers experienced communication interruptions. And in the case of A1 Telekom, the problem occurred nationwide.
Online entertainment was also targeted by cybercriminals throughout Q1. As Blizzard reported on a DDoS attack earlier this year. A large amount of junk traffic causes players, especially those trying to connect to World of Warcraft servers, to experience slow connections. There are also cases where players are dropped from the server. Towards the end of the month, cybercriminals continued to attack League of Legends. Players participating in Clash mode tournaments experienced login issues and connection interruptions. In February, a DDoS attack temporarily disabled Siminn Iceland’s television service. And in March, the LittleBigPlanet server went down for several days.

Blizzard also suffered a DDoS attack in early January 2021
In early 2021, many schools have switched to on-campus or hybrid mode. But this also does not prevent DDoS attacks. Instead of flooding online platforms with junk traffic, hackers seek to gain access to the internet of educational institutions. Specifically, in February, schools in the United States in the states of Winthrop, Massachusetts, and Manchester Township, New Jersey, were attacked by DDoS. In some cases, cybercriminals forced educational institutions to temporarily return to distance learning. In March, the school CSG Comenius Mariënburg - Netherlands was also the victim of a DDoS attack. This attack was determined to be caused by students. Although the two students were quickly identified, the school suspected there were other accomplices.
The most important event in the first quarter of this year is vaccination against COVID-19. Once the vaccination population segmentation was complete, the sites involved were disrupted. In late January, a vaccine registration website in the US state of Minnesota crashed. The incident happened to coincide with the opening time of appointments for seniors, teachers, and childcare workers. In January, a similar incident occurred on the vaccine appointment portal in Massachusetts. Retired, chronically ill or employees of senior housing estates were not able to access it. In either case, no one knows for sure if it was a DDoS attack or a legitimate traffic flow. In addition, cybersecurity company Imperva has also noticed a spike in bot activity in healthcare sources.
Politics also did not escape the DDoS attack in Q1 of this year. Last February, cybercriminals flooded the websites of Dutch politician Kati Piri with small amounts of traffic. The Labor Party website suffered the same fate because she was a member of that Party. Later, the Turkish group Anka Nefeler Tim claimed responsibility for this attack. At the end of March, a DDoS attack occurred on the website of the Chinese Parliamentary Alliance (IPAC). An IPAC representative said this is not the first DDoS attack on IPAC. In addition, several government agencies in Russia and Ukraine have reported DDoS attacks as early as 2021. The victims include the websites of the Russian Federal Penitentiary Service and the National Guard, the Government of the Russian Federation. Kiev City State Authority, Security Service of Ukraine, National Security and Defense Council, as well as other security and defense organizations of Ukraine.

DDoS attack on Dutch politician Kati Piri .’s website
Since the beginning of 2021, a number of media outlets in Russia and other countries have been targeted by DDoS attacks. In January, attackers took down the website of the Kazakh newspaper Vlast. Or the Brazilian non-profit media organization Repórter Brasil was also attacked for six consecutive days. The Ulpressa portal in the Russian city of Ulyanovsk suffered an attack that lasted several weeks. This site is hacked every day during peak hours. Initially, the KazanFirst portal managed to repel spam traffic. But the attackers changed tactics and eventually took the site offline. A similar scenario occurs in the case of the Mexican magazine Espejo. The administrators tried to deflect the traffic, but then there was a stronger wave of DDoS.
It’s not just legitimate organizations that were hit by Distributed Denial of Service attacks in Q1 2021. In January, many resources on the anonymous Tor network were disrupted. This is a pretty popular network with cybercriminals. The Tor network may have been overwhelmed by DDoS attacks against specific websites on the Dark Web. February’s target is the large underground forum Dread. This is a forum used to discuss black market transactions. Forum administrators were forced to connect additional servers to combat this attack.
However, this quarter still has other positive results. Some DDoS organizations have been exposed. Like the duo of high-ranked players in Apex Legends who DDoS attacks whoever defeats them. And in the end they were banned. At the end of last year, a teenager was subjected to more severe punishment. Because he tried to crash the Miami-Dade County Public Schools online learning system. Although he didn’t go to jail, he did 30 hours of community service and was placed on probation.
Denial of Service Attack Trends in Q1

Cryptocurrencies and Bitcoin Price Drops Increase DDoS Attacks
In Q1 2021, the DDoS market grew by about 30% compared to the reported forecast, surpassing the 40% mark. Interestingly, 43% of attacks occurred relatively normally in January.
The unexpected increase in DDoS activity can be attributed to the fact that the price of cryptocurrencies in general and Bitcoin, in particular, began to decline in January of this year. In fact, in previous years, the increase in the price of cryptocurrencies caused DDoS attacks to decrease. As a result, DDoS activities show signs of a resurgence when a drop in cryptocurrency prices is noticed. However, it seems that the Bitcoin price has a mind of its own. It rose again in February and peaked in March. So the DDoS market fell in February and March.
The forecast for these two months is quite consistent with the current situation. The DDoS market showed a slight growth compared to Q4, but not more than 30%. It is quite interesting that the indexes of February and March this year are quite similar to January of the previous year.
The first quarter of 2019 is quite stable, at a standard level, so it can be used as a measure. Last year saw an explosion in DDoS activities in February and March. Caused by the COVID-19 epidemic, activities moved online. In addition, many new targets vulnerable to DDoS attacks have emerged. The new DDoS activities of January this year are clearly not inferior to those of 2019.
Over the past year, organizations have learned to protect their infrastructure when implementing remote work. Therefore, in Q1 there was not much fluctuation. However, this year’s drop in attack figures is due to the previous year’s high volatility, not this year’s drop. At the same time, the share of smart attacks in Q1 has increased compared to the end of 2020 (from 44.29% to 44.60%).
The Q4 2020 report noted a new trend in attacks. The duration of short attacks has been reduced. In contrast, the duration of long attacks has increased. This trend also continued this quarter. It can be seen clearly in the time to attack data compared to Q4 of the previous year. And experts say this trend is likely to continue into the future.
Distributed Denial of Service Attack Stats

NETSCOUT reports 5.4 million attacks in the first half of 2021
1. Methodology applied to DDoS attack situation
If the interval between the uptime of the botnet is not more than 24 hours, it is considered a single attack. Conversely, if the website is attacked by the same botnet for 24 hours or more, it is considered two attacks. Bot requests from different botnets targeting the same target are also considered separate attacks.
The location of the DDoS attack victim and the C&C server used to send the command are determined by their respective IP addresses. The number of unique targets of DDoS attacks is the number of unique IP addresses in the quarterly statistics.
Smart DDoS stats are limited to botnets. And botnets are just one of the tools used in DDoS attacks. This section does not cover every single DDoS attack that occurred during the review period.
2. Distributed Denial of Service attack summary of Q1
In the first quarter of 2021:
- The United States overtook China as the leader in the number of DDoS attacks and the number of unique targets.
- DDoS activity surged in January, peaking with more than 1,800 attacks per day. 1,833 attacks on the 10th and 1,820 attacks on the 11th. On some other days in January, the number of attacks exceeded 1,500.
- Attacks occurred fairly evenly throughout the week.
- The number of short attacks (under 4 hours) has increased significantly.
- The most common attack type is UDP flooding (41.87%). While SYN flooding fell to 3rd place (26.36%)
- Linux botnets continue to account for the majority of DDoS traffic (99.9%).
3. Regional DDoS attack
In the first quarter of 2021, there was a change in the ranking of countries with the most DDoS attacks. Topping the chart was the United States (37.82%), up 16.84 p.p. China dropped to 2nd place (16.64%), down 42.31 p.p compared to the previous period. Hong Kong Special Administrative Region (2.67%) fell from 3rd place to 9th place. And Canada has replaced Hong Kong in 3rd place (4.94%).
Top 10 countries by the number of DDoS targets. Led by the US (41.98%), up 18.41 p.p. In contrast, China fell more than 4 times - from 44.49% to 10.77%, falling to second place. However, there are some slight differences in the two charts above. Hong Kong has been dropped out of the Top 10 countries in terms of the number of targets. And the Netherlands took third place (4.90%).
4. Distributed Denial of Service Attack
The first quarter of 2021 has gotten off to a pretty “exciting” start. DDoS activity peaked on January 10 and 11, when the number of attacks exceeded 1,800 per day. The number of days with more than 1,500 attacks increased in January. That increase is most likely due to the short-term drop in the bitcoin price.
After a stormy start, February, on the other hand, was relatively calm. For several consecutive days, from the 13th to the 17th, the number of DDoS attacks remained below 500. Of which, February 13 only recorded 346 attacks. But the beginning of March saw another increase, but less than January. With 1,311 attacks on the 3rd and 1,290 on the 4th. This was due to the drop in the price of Bitcoin.
In Q1/2021, DDoS attacks by day of the week were more evenly distributed than in the previous period. Saturday is the day with the most number of attacks (15.44%). While Thursday (13.12%), which was the most attacked day in the previous quarter, ranked last this quarter. Overall, weekday attack rates increased in the first quarter of 2021.
5. Duration and Types of Distributed Denial of Service Attacks
The average DDoS attack duration in Q1 decreased by more than half compared to Q4 2020. The percentage of short attacks (under 4 hours) has increased markedly. In contrast, the rate of long attacks decreased. Attacks lasting 5-9 hours dropped 7.64 p.p, representing 4.14% of total attacks. The ratio of long (0.07%) and extra long (0.13%) attacks also decreased slightly.
The distribution of attack patterns continues to change. In Q1 2021, SYN flooding (26.36%) fell from 1st place to 3rd place. Meanwhile, UDP flooding (41.87%) and TCP flooding (29.23%) were used more. . GRE (1.43%) and HTTP flooding (1.10%) also showed modest growth.
In terms of botnets, Linux-based bots accounted for the majority of attacks this quarter. Moreover, their proportion also increased slightly compared to the previous period, from 99.8% to 99.9%.
6. Distribute botnet DDoS attacks by geographical location
The US-led in terms of C&C server hosting (41.31%) in Q1, up 5.01 p.p. qoq. Germany (15.32%) and the Netherlands (14.91%) continue to hold the 2nd and 3rd positions. However, the market share of the Netherlands decreased, while that of Germany nearly doubled.
Romania dropped from 4th to 7th (2.46%), behind France (3.97%), Great Britain (3.01%), and Russia (2.60%). Canada holds the 8th position (1.92%), while Singapore and Seychelles are at the bottom of the table, both accounting for 1.37% in Q1.
Summary of DDoS attack situation
The first quarter of this year saw an increase in DDoS activities due to falling cryptocurrency prices. But in general, the DDoS attack situation does not have large fluctuations. At the same time, there has also been a big change in the rankings of DDoS attacks. The US overtook China to the top spot in terms of the number of DDoS attacks and the number of DDoS targets. The most common type of attack SYN flooding has given way to UDP and TCP.
The DDoS market forecast will not change significantly in Q2. As usual, DDoS activity is largely dependent on cryptocurrency prices. Currently, the cryptocurrency price is hitting its all-time high. Besides, based on the developments of previous years, the second quarter is usually quieter. So, unless there is a big swing, Q2 is likely to see a slight decline. If the crypto market plummets, DDoS activity will increase. The majority will be simple and prolonged attacks.
From the above statistics, although DDoS activities do not have large fluctuations, there is no doubt about how dangerous and complex they are. Faced with that situation, VNETWORK always wants to be able to support businesses safely in the Internet environment. With VNIS - a comprehensive website security solution (layer 3/4/7 protection), dedicated to digital businesses, Anti DDoS attacks with the largest traffic.
If you have any questions regarding email security, website security, anti-DDoS, or Data Center services,… please leave a message, our experts will assist you.

